-
The Iranian hacking group known as MuddyWater has been observed leveraging a new backdoor dubbed UDPGangster that uses the User Datagram Protocol (UDP) for command-and-control (C2) purposes. The cyber espionage activity targeted users in Turkey, Israel, and Azerbaijan, according to a report from Fortinet FortiGuard Labs. “This malware enables remote control of compromised systems by allowing
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
·
SIMI VALLEY, California—Last summer’s $156 billion one-time boost for defense spending through the reconciliation bill is likely “only just the beginning,” the defense secretary said on Saturday.“The President has said, and continues to say, he's committed to rebuilding the military, and that requires spending, and substantial spending,” Pete Hegseth said during his keynote address at the Reagan National Defense Forum Saturday. “Just this week, and I was with some of you, was there in the Oval [Office] having these very discussions about FY26 and FY27. And all I can say today is the President is committed to ensuring that our services, our great companies, our industries, have what is needed.”
That funding, he said, will be key to “supercharging” the defense industry—one of the Pentagon’s four “lines of effort,” along with homeland defense, pushing allies to increase defense spending, and deterring China without engaging in conflict.
“We received a historic boost in funding last year, and believe that is only just the beginning,” Hegseth said, alluding to the $156 billion boost from budget reconciliation on top of the DOD’s proposed budget for 2026. “We need a revived defense industrial base. We need those capabilities. We need them yesterday. And so, resource-wise, I think this room will be encouraged by what we'll see soon—but I don't want to get too ahead.”
U.S. defense spending has risen in recent years from $812.1 billion in fiscal year 2017 to $870.7 billion in fiscal year 2021 to $895.2 billion in 2025, according to a Center for Strategic and International Studies analysis. But defense hawks argue that inflation tempers any real growth in national security spending.
Hegseth added that budget and resource concerns are “what keeps me up,” along with military operations.
His comments come just days after the White House released its National Security Strategy, which put some emphasis on defense production.
“We want the world’s most robust industrial base. American national power depends on a strong industrial sector capable of meeting both peacetime and wartime production demands,” the document states. “That requires not only direct defense industrial production capacity but also defense-related production capacity.”
Some analysts had noted that the one-time reconciliation boost could lead the Pentagon to launch programs that would be unsustainable without further spending.
The White House is considering asking for a second reconciliation bill next year, Office of Management and Budget Director Russell Vought said Saturday at the event.
The reconciliation funding, much of which is marked for use during 2026, “allowed us to get all of these priorities—Golden Dome, shipbuilding, nuclear modernization—in a mandatory account that now has certainty. So, that's not subject to the highs and lows of the appropriations process,” Vought said. “Have we made a decision yet on another reconciliation bill? No, we have not. We will make sure that we continue to grow. There will not be a hole there. But I think it is a paradigm shift that we're excited about.”
]]>¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Over 30 security vulnerabilities have been disclosed in various artificial intelligence (AI)-powered Integrated Development Environments (IDEs) that combine prompt injection primitives with legitimate features to achieve data exfiltration and remote code execution. The security shortcomings have been collectively named IDEsaster by security researcher Ari Marzouk (MaccariTA), who discovered them
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
·
A Little Sunshine, Alexander Korsukov, Alexey Pokatilo, AW Tech Limited, Awesome Technologies, Brian Mellor, CLS Research LTD, Filip Perkon, Geekly Solutions Ltd, Livingston Research, Marina Butina, NatInfoSec, North Data, OK Marketing LTD, Olekszij Pokatilo, Proglobal Solutions LTD, Russia’s War on Ukraine, Russian Business Week, Russian Diplomatic Online Club, Synergy, Synergy University, Tweetsquad, Two Sigma Solutions LTD, Vadim Lobov, VLS Research LTDA sprawling academic cheating network turbocharged by Google Ads that has generated nearly $25 million in revenue has curious ties to a Kremlin-connected oligarch whose Russian university builds drones for Russia’s war against Ukraine.
The Nerdify homepage.
The link between essay mills and Russian attack drones might seem improbable, but understanding it begins with a simple question: How does a human-intensive academic cheating service stay relevant in an era when students can simply ask AI to write their term papers? The answer – recasting the business as an AI company – is just the latest chapter in a story of many rebrands that link the operation to Russia’s largest private university.
Search in Google for any terms related to academic cheating services — e.g., “help with exam online” or “term paper online” — and you’re likely to encounter websites with the words “nerd” or “geek” in them, such as thenerdify[.]com and geekly-hub[.]com. With a simple request sent via text message, you can hire their tutors to help with any assignment.
These nerdy and geeky-branded websites frequently cite their “honor code,” which emphasizes they do not condone academic cheating, will not write your term papers for you, and will only offer support and advice for customers. But according to This Isn’t Fine, a Substack blog about contract cheating and essay mills, the Nerdify brand of websites will happily ignore that mantra.
“We tested the quick SMS for a price quote,” wrote This Isn’t Fine author Joseph Thibault. “The honor code references and platitudes apparently stop at the website. Within three minutes, we confirmed that a full three-page, plagiarism- and AI-free MLA formatted Argumentative essay could be ours for the low price of $141.”
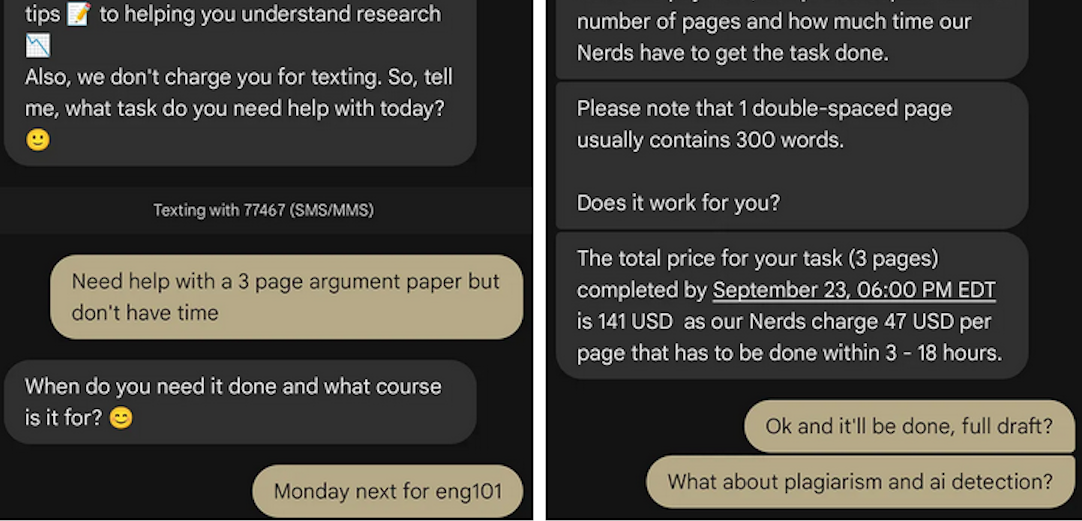
A screenshot from Joseph Thibault’s Substack post shows him purchasing a 3-page paper with the Nerdify service.
Google prohibits ads that “enable dishonest behavior.” Yet, a sprawling global essay and homework cheating network run under the Nerdy brands has quietly bought its way to the top of Google searches – booking revenues of almost $25 million through a maze of companies in Cyprus, Malta and Hong Kong, while pitching “tutoring” that delivers finished work that students can turn in.
When one Nerdy-related Google Ads account got shut down, the group behind the company would form a new entity with a front-person (typically a young Ukrainian woman), start a new ads account along with a new website and domain name (usually with “nerdy” in the brand), and resume running Google ads for the same set of keywords.
UK companies belonging to the group that have been shut down by Google Ads since Jan 2025 include:
–Proglobal Solutions LTD (advertised nerdifyit[.]com);
–AW Tech Limited (advertised thenerdify[.]com);
–Geekly Solutions Ltd (advertised geekly-hub[.]com).Currently active Google Ads accounts for the Nerdify brands include:
-OK Marketing LTD (advertising geekly-hub[.]net), formed in the name of Olha Karpenko, a young Ukrainian woman;
–Two Sigma Solutions LTD (advertising litero[.]ai), formed in the name of Olekszij (Alexey) Pokatilo.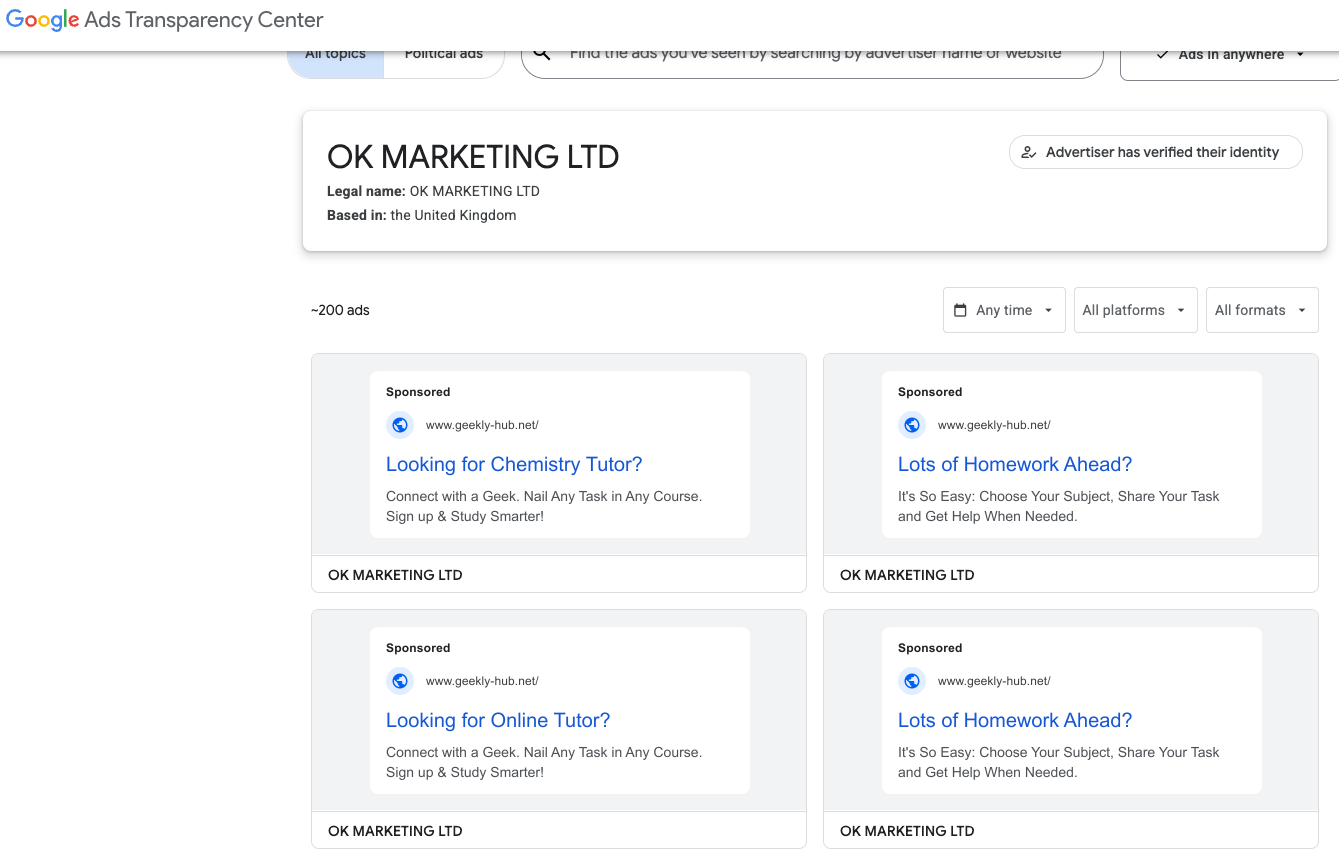
Google’s Ads Transparency page for current Nerdify advertiser OK Marketing LTD.
Mr. Pokatilo has been in the essay-writing business since at least 2009, operating a paper-mill enterprise called Livingston Research alongside Alexander Korsukov, who is listed as an owner. According to a lengthy account from a former employee, Livingston Research mainly farmed its writing tasks out to low-cost workers from Kenya, Philippines, Pakistan, Russia and Ukraine.
Pokatilo moved from Ukraine to the United Kingdom in Sept. 2015 and co-founded a company called Awesome Technologies, which pitched itself as a way for people to outsource tasks by sending a text message to the service’s assistants.
The other co-founder of Awesome Technologies is 36-year-old Filip Perkon, a Swedish man living in London who touts himself as a serial entrepreneur and investor. Years before starting Awesome together, Perkon and Pokatilo co-founded a student group called Russian Business Week while the two were classmates at the London School of Economics. According to the Bulgarian investigative journalist Christo Grozev, Perkon’s birth certificate was issued by the Soviet Embassy in Sweden.

Alexey Pokatilo (left) and Filip Perkon at a Facebook event for startups in San Francisco in mid-2015.
Around the time Perkon and Pokatilo launched Awesome Technologies, Perkon was building a social media propaganda tool called the Russian Diplomatic Online Club, which Perkon said would “turbo-charge” Russian messaging online. The club’s newsletter urged subscribers to install in their Twitter accounts a third-party app called Tweetsquad that would retweet Kremlin messaging on the social media platform.
Perkon was praised by the Russian Embassy in London for his efforts: During the contentious Brexit vote that ultimately led to the United Kingdom leaving the European Union, the Russian embassy in London used this spam tweeting tool to auto-retweet the Russian ambassador’s posts from supporters’ accounts.
Neither Mr. Perkon nor Mr. Pokatilo replied to requests for comment.
A review of corporations tied to Mr. Perkon as indexed by the business research service North Data finds he holds or held director positions in several U.K. subsidiaries of Synergy University, Russia’s largest private education provider. Synergy has more than 35,000 students, and sells T-shirts with patriotic slogans such as “Crimea is Ours,” and “The Russian Empire — Reloaded.”
The president of Synergy University is Vadim Lobov, a Kremlin insider whose headquarters on the outskirts of Moscow reportedly features a wall-sized portrait of Russian President Vladimir Putin in the pop-art style of Andy Warhol. For a number of years, Lobov and Perkon co-produced a cross-cultural event in the U.K. called Russian Film Week.

Synergy President Vadim Lobov and Filip Perkon, speaking at a press conference for Russian Film Week, a cross-cultural event in the U.K. co-produced by both men.
Mr. Lobov was one of 11 individuals reportedly hand-picked by the convicted Russian spy Marina Butina to attend the 2017 National Prayer Breakfast held in Washington D.C. just two weeks after President Trump’s first inauguration.
While Synergy University promotes itself as Russia’s largest private educational institution, hundreds of international students tell a different story. Online reviews from students paint a picture of unkept promises: Prospective students from Nigeria, Kenya, Ghana, and other nations paying thousands in advance fees for promised study visas to Russia, only to have their applications denied with no refunds offered.
“My experience with Synergy University has been nothing short of heartbreaking,” reads one such account. “When I first discovered the school, their representative was extremely responsive and eager to assist. He communicated frequently and made me believe I was in safe hands. However, after paying my hard-earned tuition fees, my visa was denied. It’s been over 9 months since that denial, and despite their promises, I have received no refund whatsoever. My messages are now ignored, and the same representative who once replied instantly no longer responds at all. Synergy University, how can an institution in Europe feel comfortable exploiting the hopes of Africans who trust you with their life savings? This is not just unethical — it’s predatory.”
This pattern repeats across reviews by multilingual students from Pakistan, Nepal, India, and various African nations — all describing the same scheme: Attractive online marketing, promises of easy visa approval, upfront payment requirements, and then silence after visa denials.
Reddit discussions in r/Moscow and r/AskARussian are filled with warnings. “It’s a scam, a diploma mill,” writes one user. “They literally sell exams. There was an investigation on Rossiya-1 television showing students paying to pass tests.”
The Nerdify website’s “About Us” page says the company was co-founded by Pokatilo and an American named Brian Mellor. The latter identity seems to have been fabricated, or at least there is no evidence that a person with this name ever worked at Nerdify.
Rather, it appears that the SMS assistance company co-founded by Messrs. Pokatilo and Perkon (Awesome Technologies) fizzled out shortly after its creation, and that Nerdify soon adopted the process of accepting assignment requests via text message and routing them to freelance writers.
A closer look at an early “About Us” page for Nerdify in The Wayback Machine suggests that Mr. Perkon was the real co-founder of the company: The photo at the top of the page shows four people wearing Nerdify T-shirts seated around a table on a rooftop deck in San Francisco, and the man facing the camera is Perkon.

Filip Perkon, top right, is pictured wearing a Nerdify T-shirt in an archived copy of the company’s About Us page. Image: archive.org.
Where are they now? Pokatilo is currently running a startup called Litero.Ai, which appears to be an AI-based essay writing service. In July 2025, Mr. Pokatilo received pre-seed funding of $800,000 for Litero from an investment program backed by the venture capital firms AltaIR Capital, Yellow Rocks, Smart Partnership Capital, and I2BF Global Ventures.
Meanwhile, Filip Perkon is busy setting up toy rubber duck stores in Miami and in at least three locations in the United Kingdom. These “Duck World” shops market themselves as “the world’s largest duck store.”
This past week, Mr. Lobov was in India with Putin’s entourage on a charm tour with India’s Prime Minister Narendra Modi. Although Synergy is billed as an educational institution, a review of the company’s sprawling corporate footprint (via DNS) shows it also is assisting the Russian government in its war against Ukraine.

Synergy University President Vadim Lobov (right) pictured this week in India next to Natalia Popova, a Russian TV presenter known for her close ties to Putin’s family, particularly Putin’s daughter, who works with Popova at the education and culture-focused Innopraktika Foundation.
The website bpla.synergy[.]bot, for instance, says the company is involved in developing combat drones to aid Russian forces and to evade international sanctions on the supply and re-export of high-tech products.
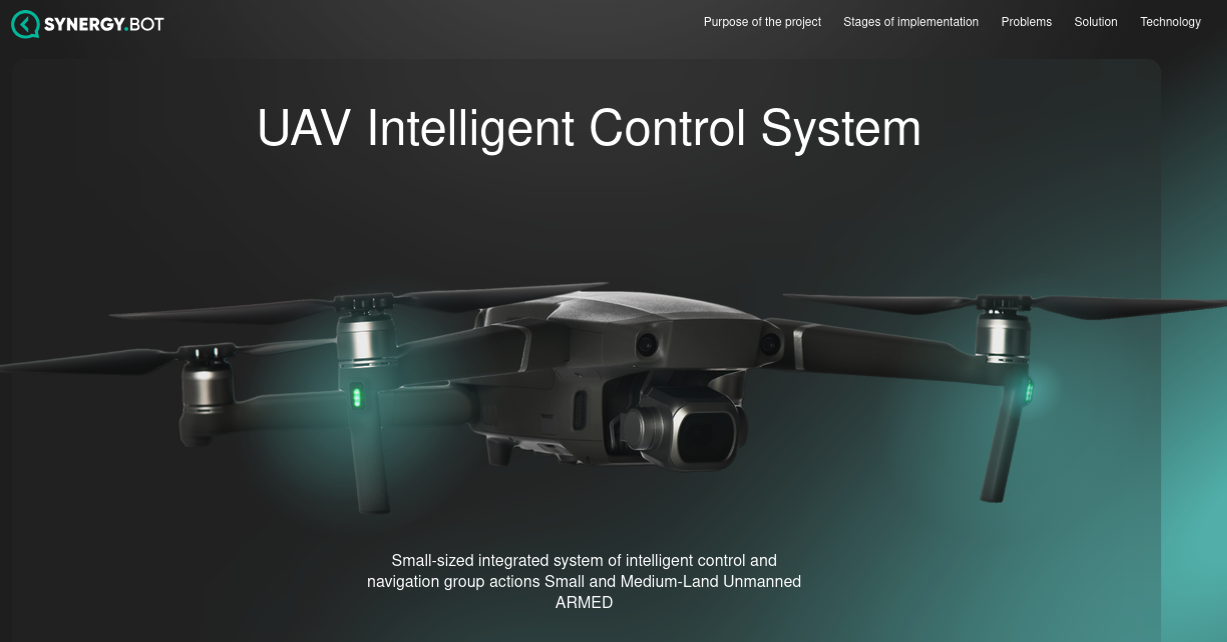
A screenshot from the website of synergy,bot shows the company is actively engaged in building armed drones for the war in Ukraine.
KrebsOnSecurity would like to thank the anonymous researcher NatInfoSec for their assistance in this investigation.
Update, Dec. 8, 10:06 a.m. ET: Mr. Pokatilo responded to requests for comment after the publication of this story. Pokatilo said he has no relation to Synergy nor to Mr. Lobov, and that his work with Mr. Perkon ended with the dissolution of Awesome Technologies.
“I have had no involvement in any of his projects and business activities mentioned in the article and he has no involvement in Litero.ai,” Pokatilo said of Perkon.
Mr. Pokatilo said his new company Litero “does not provide contract cheating services and is built specifically to improve transparency and academic integrity in the age of universal use of AI by students.”
“I am Ukrainian,” he said in an email. “My close friends, colleagues, and some family members continue to live in Ukraine under the ongoing invasion. Any suggestion that I or my company may be connected in any way to Russia’s war efforts is deeply offensive on a personal level and harmful to the reputation of Litero.ai, a company where many team members are Ukrainian.”
Update, Dec. 11, 12:07 p.m. ET: Mr. Perkon responded to requests for comment after the publication of this story. Perkon said the photo of him in a Nerdify T-shirt (see screenshot above) was taken after a startup event in San Francisco, where he volunteered to act as a photo model to help friends with their project.
“I have no business or other relations to Nerdify or any other ventures in that space,” Mr. Perkon said in an email response. “As for Vadim Lobov, I worked for Venture Capital arm at Synergy until 2013 as well as his business school project in the UK, that didn’t get off the ground, so the company related to this was made dormant. Then Synergy kindly provided sponsorship for my Russian Film Week event that I created and ran until 2022 in the U.K., an event that became the biggest independent Russian film festival outside of Russia. Since the start of the Ukraine war in 2022 I closed the festival down.”
“I have had no business with Vadim Lobov since 2021 (the last film festival) and I don’t keep track of his endeavours,” Perkon continued. “As for Alexey Pokatilo, we are university friends. Our business relationship has ended after the concierge service Awesome Technologies didn’t work out, many years ago.”
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday formally added a critical security flaw impacting React Server Components (RSC) to its Known Exploited Vulnerabilities (KEV) catalog following reports of active exploitation in the wild. The vulnerability, CVE-2025-55182 (CVSS score: 10.0), relates to a case of remote code execution that could be triggered by an
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A new agentic browser attack targeting Perplexity’s Comet browser that’s capable of turning a seemingly innocuous email into a destructive action that wipes a user’s entire Google Drive contents, findings from Straiker STAR Labs show. The zero-click Google Drive Wiper technique hinges on connecting the browser to services like Gmail and Google Drive to automate routine tasks by granting them
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A critical security flaw has been disclosed in Apache Tika that could result in an XML external entity (XXE) injection attack. The vulnerability, tracked as CVE-2025-66516, is rated 10.0 on the CVSS scoring scale, indicating maximum severity. “Critical XXE in Apache Tika tika-core (1.13-3.2.1), tika-pdf-module (2.0.0-3.2.1) and tika-parsers (1.13-1.28.5) modules on all platforms allows an
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
This week in cybersecurity from the editors at Cybercrime Magazine
 Sausalito, Calif. – Dec. 5, 2025
Sausalito, Calif. – Dec. 5, 2025– Read the full story in Bolde
High school students and parents, listen up!
Some fields are skyrocketing in demand, offering promising career prospects and competitive salaries. However, gaining entry into college programs often requires a solid GPA to ensure you’re prepared for the rigorous coursework ahead. Cybersecurity is one of the most in demand fields that require you to study hard to ensure you get the GPA you need to make your academic dreams a reality, according to a recent Bolde article.
In an age where data breaches are increasingly common, cybersecurity is more critical than ever. This field focuses on protecting computer systems and networks from digital attacks. To enter a reputable cybersecurity program, you’ll need a GPA of around 3.0, with more competitive programs requiring higher. The coursework includes computer science, network security, and ethical hacking.
Beyond academic credentials, problem-solving skills and an analytical mindset are essential. According to Cybersecurity Ventures, the field is expected to see millions of unfilled jobs in the coming years, underscoring the growing demand. Internships and certifications can significantly boost your employability in this fast-paced industry. If you’re someone who loves a good challenge and wants to keep data safe, cybersecurity is an exciting and ever-evolving field to consider.
The tech industry is booming, and computer science is at the heart of it all. Whether you’re interested in software development, AI, or cybersecurity, a degree in computer science can open countless doors. Most reputable programs look for a GPA of at least 3.0, although the more competitive institutions may require a 3.5 or higher. The curriculum is heavy on math and logic, so it’s critical to bring your analytical A-game.
Bolde also takes a look at other in demand fields including nursing, data science, finance, engineering, psychology, business administration, environmental science, marketing, education, and healthcare administration.
Cybercrime Magazine is Page ONE for Cybersecurity. Go to any of our sections to read the latest:
- SCAM. The latest schemes, frauds, and social engineering attacks being launched on consumers globally.
- NEWS. Breaking coverage on cyberattacks and data breaches, and the most recent privacy and security stories.
- HACK. Another organization gets hacked every day. We tell you who, what, where, when, and why.
- VC. Cybersecurity venture capital deal flow with the latest investment activity from various sources around the world.
- M&A. Cybersecurity mergers and acquisitions including big tech, pure cyber, product vendors and professional services.
- BLOG. What’s happening at Cybercrime Magazine. Plus the stories that don’t make headlines (but maybe they should).
- PRESS. Cybersecurity industry news and press releases in real time from the editors at Business Wire.
- PODCAST. New episodes daily on the Cybercrime Magazine Podcast feature victims, law enforcement, vendors, and cybersecurity experts.
- RADIO. Tune into WCYB Digital Radio at Cybercrime.Radio, the first and only round-the-clock internet radio station devoted to cybersecurity.
Contact us to send story tips, feedback and suggestions, and for sponsorship opportunities and custom media productions.
The post Here’s What GPA You Need To Study In The Cybersecurity Field appeared first on Cybercrime Magazine.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
China-based phishing groups blamed for non-stop scam SMS messages about a supposed wayward package or unpaid toll fee are promoting a new offering, just in time for the holiday shopping season: Phishing kits for mass-creating fake but convincing e-commerce websites that convert customer payment card data into mobile wallets from Apple and Google. Experts say these same phishing groups also are now using SMS lures that promise unclaimed tax refunds and mobile rewards points.
Over the past week, thousands of domain names were registered for scam websites that purport to offer T-Mobile customers the opportunity to claim a large number of rewards points. The phishing domains are being promoted by scam messages sent via Apple’s iMessage service or the functionally equivalent RCS messaging service built into Google phones.
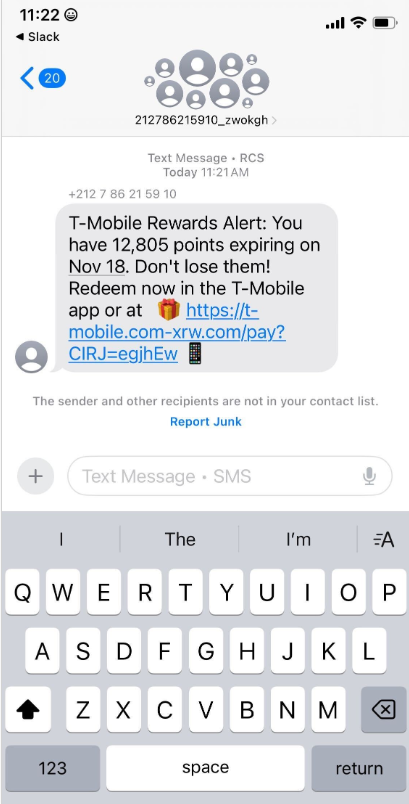
An instant message spoofing T-Mobile says the recipient is eligible to claim thousands of rewards points.
The website scanning service urlscan.io shows thousands of these phishing domains have been deployed in just the past few days alone. The phishing websites will only load if the recipient visits with a mobile device, and they ask for the visitor’s name, address, phone number and payment card data to claim the points.
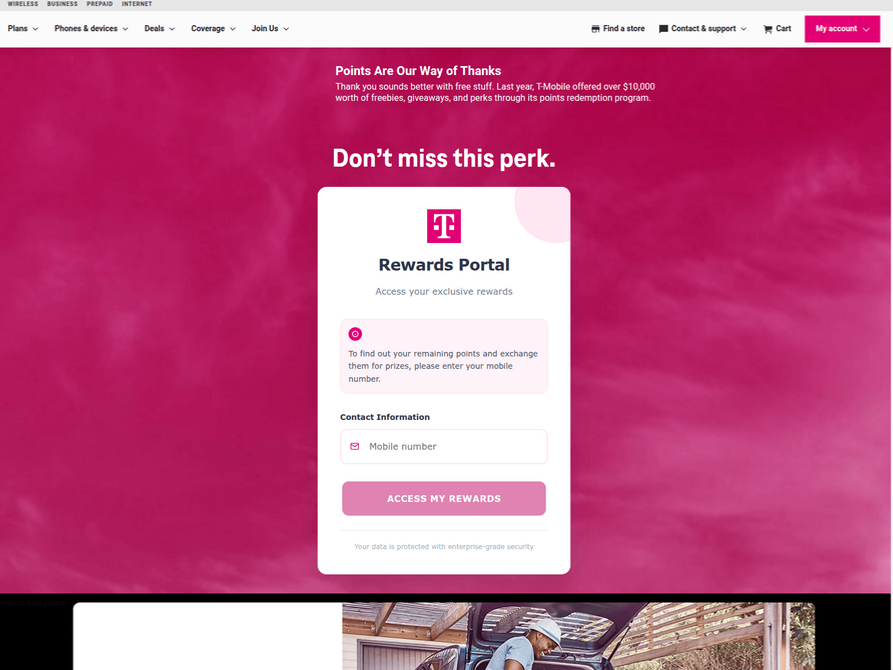
A phishing website registered this week that spoofs T-Mobile.
If card data is submitted, the site will then prompt the user to share a one-time code sent via SMS by their financial institution. In reality, the bank is sending the code because the fraudsters have just attempted to enroll the victim’s phished card details in a mobile wallet from Apple or Google. If the victim also provides that one-time code, the phishers can then link the victim’s card to a mobile device that they physically control.
Pivoting off these T-Mobile phishing domains in urlscan.io reveals a similar scam targeting AT&T customers:
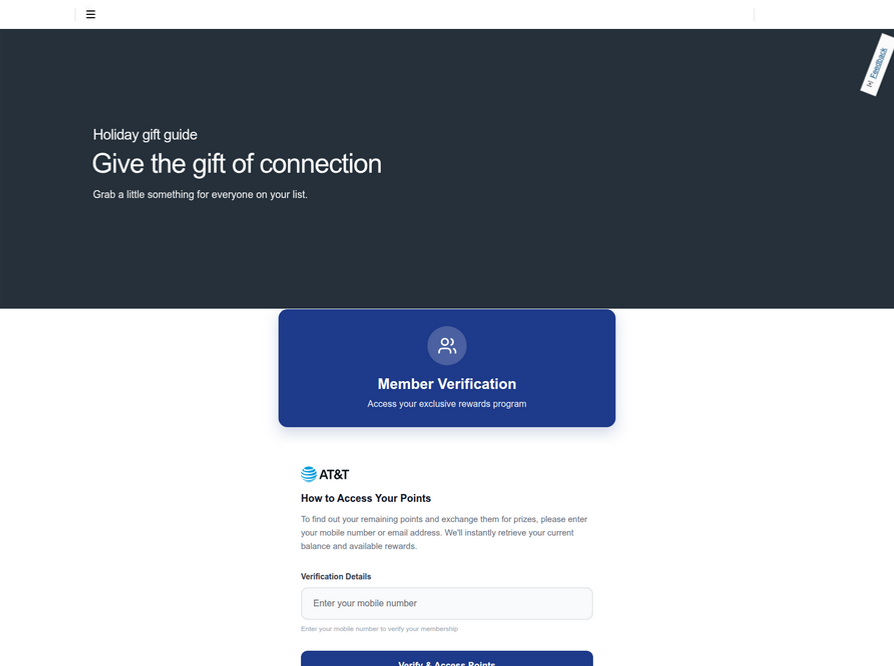
An SMS phishing or “smishing” website targeting AT&T users.
Ford Merrill works in security research at SecAlliance, a CSIS Security Group company. Merrill said multiple China-based cybercriminal groups that sell phishing-as-a-service platforms have been using the mobile points lure for some time, but the scam has only recently been pointed at consumers in the United States.
“These points redemption schemes have not been very popular in the U.S., but have been in other geographies like EU and Asia for a while now,” Merrill said.
A review of other domains flagged by urlscan.io as tied to this Chinese SMS phishing syndicate shows they are also spoofing U.S. state tax authorities, telling recipients they have an unclaimed tax refund. Again, the goal is to phish the user’s payment card information and one-time code.
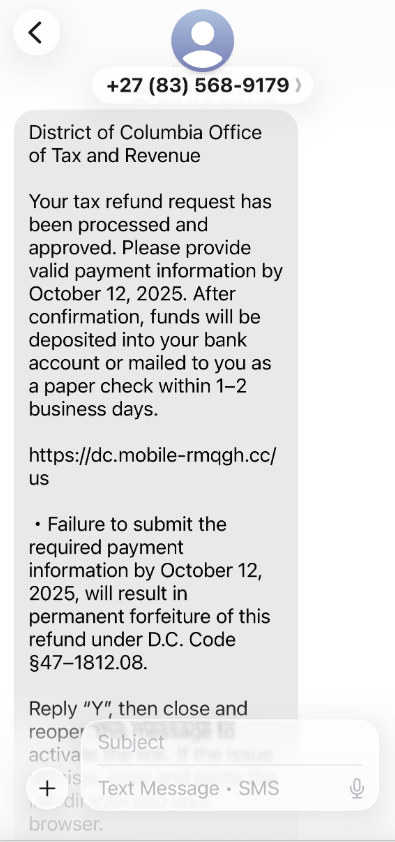
A text message that spoofs the District of Columbia’s Office of Tax and Revenue.
CAVEAT EMPTOR
Many SMS phishing or “smishing” domains are quickly flagged by browser makers as malicious. But Merrill said one burgeoning area of growth for these phishing kits — fake e-commerce shops — can be far harder to spot because they do not call attention to themselves by spamming the entire world.
Merrill said the same Chinese phishing kits used to blast out package redelivery message scams are equipped with modules that make it simple to quickly deploy a fleet of fake but convincing e-commerce storefronts. Those phony stores are typically advertised on Google and Facebook, and consumers usually end up at them by searching online for deals on specific products.
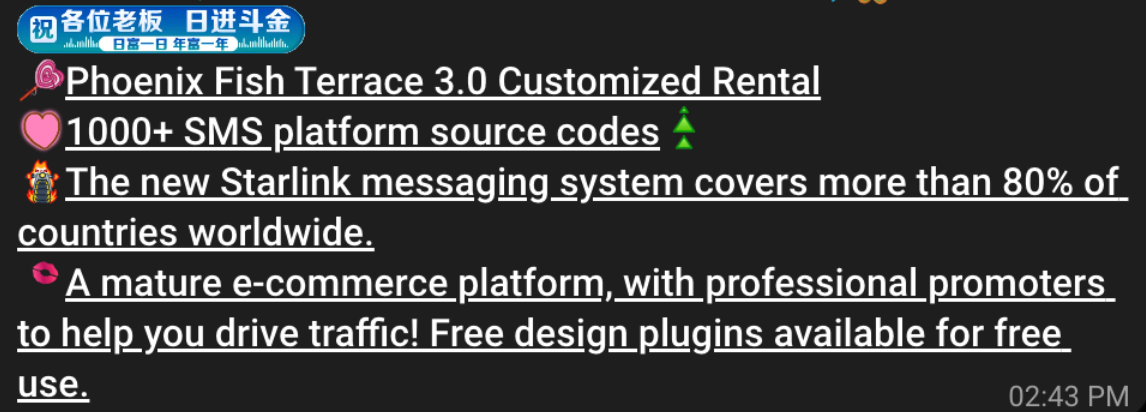
A machine-translated screenshot of an ad from a China-based phishing group promoting their fake e-commerce shop templates.
With these fake e-commerce stores, the customer is supplying their payment card and personal information as part of the normal check-out process, which is then punctuated by a request for a one-time code sent by your financial institution. The fake shopping site claims the code is required by the user’s bank to verify the transaction, but it is sent to the user because the scammers immediately attempt to enroll the supplied card data in a mobile wallet.
According to Merrill, it is only during the check-out process that these fake shops will fetch the malicious code that gives them away as fraudulent, which tends to make it difficult to locate these stores simply by mass-scanning the web. Also, most customers who pay for products through these sites don’t realize they’ve been snookered until weeks later when the purchased item fails to arrive.
“The fake e-commerce sites are tough because a lot of them can fly under the radar,” Merrill said. “They can go months without being shut down, they’re hard to discover, and they generally don’t get flagged by safe browsing tools.”
Happily, reporting these SMS phishing lures and websites is one of the fastest ways to get them properly identified and shut down. Raymond Dijkxhoorn is the CEO and a founding member of SURBL, a widely-used blocklist that flags domains and IP addresses known to be used in unsolicited messages, phishing and malware distribution. SURBL has created a website called smishreport.com that asks users to forward a screenshot of any smishing message(s) received.
“If [a domain is] unlisted, we can find and add the new pattern and kill the rest” of the matching domains, Dijkxhoorn said. “Just make a screenshot and upload. The tool does the rest.”
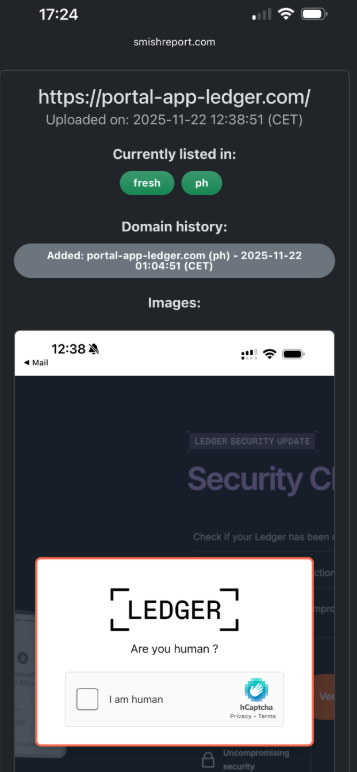
The SMS phishing reporting site smishreport.com.
Merrill said the last few weeks of the calendar year typically see a big uptick in smishing — particularly package redelivery schemes that spoof the U.S. Postal Service or commercial shipping companies.
“Every holiday season there is an explosion in smishing activity,” he said. “Everyone is in a bigger hurry, frantically shopping online, paying less attention than they should, and they’re just in a better mindset to get phished.”
SHOP ONLINE LIKE A SECURITY PRO
As we can see, adopting a shopping strategy of simply buying from the online merchant with the lowest advertised prices can be a bit like playing Russian Roulette with your wallet. Even people who shop mainly at big-name online stores can get scammed if they’re not wary of too-good-to-be-true offers (think third-party sellers on these platforms).
If you don’t know much about the online merchant that has the item you wish to buy, take a few minutes to investigate its reputation. If you’re buying from an online store that is brand new, the risk that you will get scammed increases significantly. How do you know the lifespan of a site selling that must-have gadget at the lowest price? One easy way to get a quick idea is to run a basic WHOIS search on the site’s domain name. The more recent the site’s “created” date, the more likely it is a phantom store.
If you receive a message warning about a problem with an order or shipment, visit the e-commerce or shipping site directly, and avoid clicking on links or attachments — particularly missives that warn of some dire consequences unless you act quickly. Phishers and malware purveyors typically seize upon some kind of emergency to create a false alarm that often causes recipients to temporarily let their guard down.
But it’s not just outright scammers who can trip up your holiday shopping: Often times, items that are advertised at steeper discounts than other online stores make up for it by charging way more than normal for shipping and handling.
So be careful what you agree to: Check to make sure you know how long the item will take to be shipped, and that you understand the store’s return policies. Also, keep an eye out for hidden surcharges, and be wary of blithely clicking “ok” during the checkout process.
Most importantly, keep a close eye on your monthly statements. If I were a fraudster, I’d most definitely wait until the holidays to cram through a bunch of unauthorized charges on stolen cards, so that the bogus purchases would get buried amid a flurry of other legitimate transactions. That’s why it’s key to closely review your credit card bill and to quickly dispute any charges you didn’t authorize.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Building a Secure Foundation for the Future of Autonomous Transactions

–Dr. Alissa Abdullah, Deputy Chief Security Officer, Mastercard
San Jose, Calif. – Dec. 4, 2025
Agentic commerce is changing the way we shop and interact online. Imagine telling your digital assistant to find the best deal on running shoes, make the purchase, and arrange delivery—all without you having to do a thing. This isn’t just a glimpse of the future; it’s happening now. At Mastercard, we’re excited about the possibilities, but we also know that security must keep pace with innovation.
What Is Agentic Commerce—and Why Does Security Matter?
Agentic commerce uses advanced AI agents to act on your behalf, making decisions and completing transactions autonomously. These agents can access sensitive information, negotiate with merchants, and handle complex tasks across different platforms. The benefits are clear: speed, personalization, and convenience. But with these advances come new cybersecurity challenges that we need to tackle head-on.
How Mastercard Is Protecting Agentic Commerce
At Mastercard, we focus on four key areas to keep agentic commerce secure:
- Identity and Authentication
We make sure AI agents can reliably verify who you are before taking any action. Multi-factor authentication and ongoing identity checks help prevent unauthorized transactions and keep your accounts safe. - Data Privacy
Agents handle a lot of personal and financial data. Protecting this information is a top priority. We use advanced encryption and privacy-preserving technologies to secure your data, whether it’s being sent or stored. - Transaction Security
Autonomous payments need strong protocols to block interception or fraud. Our Agent Pay solution and the Agent Payments Protocol (AP2) are designed to authenticate every transaction and provide traceability, so you can trust the process from start to finish. - Accountability and Transparency
When agents act independently, it’s important to have clear records of every action. Our systems log all activity, making it easier to resolve disputes and assign responsibility if something goes wrong. You also have control over what your agents can do and can review your transaction history anytime.
Building Trust in Autonomous Agents
Trust is the foundation of agentic commerce, but as these systems grow, it’s essential to achieve trust at scale. At Mastercard, we’re committed to building security into every layer of our systems—from the AI models that make decisions to the payment protocols that move your money.
We also believe security is a shared responsibility. Consumers should stay informed about how their data is used and take advantage of available controls. Businesses need to invest in cybersecurity and foster transparency.
Looking Ahead
Agentic commerce isn’t just a technological leap—it’s a transformation of the digital economy. As AI agents become more capable, cyber attackers will look for new ways to exploit them. Our job is to stay ahead of these threats, continuously improving our defenses and empowering users to transact with confidence.
If you’re interested in a deeper dive into the architecture, protocols, and real-world examples of agentic commerce, I encourage you to read the latest Mastercard Signals report.
At Mastercard, we believe the future of commerce should be both innovative and secure. By prioritizing cybersecurity, we’re helping unlock the full potential of autonomous agents—making commerce faster, smarter, and safer for everyone.
–Dr. Alissa Abdullah, Deputy Chief Security Officer, Mastercard
 SPONSORED BY MASTERCARD
SPONSORED BY MASTERCARDMastercard works to connect and power an inclusive digital economy that benefits everyone, everywhere by making transactions safe, simple, smart and accessible. Using secure data and networks, partnerships and passion, our innovations and solutions help individuals, financial institutions, governments and businesses realize their greatest potential. Our decency quotient, or DQ, drives our culture and everything we do inside and outside of our company.
The post Cybersecurity in Agentic Commerce: Safeguarding the Autonomous Future appeared first on Cybercrime Magazine.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
- Identity and Authentication


