Developers are unintentionally exposing passwords, API keys, and sensitive data in production information into online formatting tools such as JSONFormatter and CodeBeautify.
New research from watchTowr shows that thousands of secrets from critical organizations have been publicly accessible for years through these seemingly harmless utilities.
Online code and JSON formatters are popular among developers who want to tidy up messy data quickly. Users paste in JSON blobs, configuration files, or scripts and get neatly formatted output.
The problem begins when they use additional features, such as the “Save” button, which stores the data and generates a shareable URL.
Many users appear unaware that this means their content is permanently stored and publicly accessible to anyone with the link – and that these links are easy to enumerate.
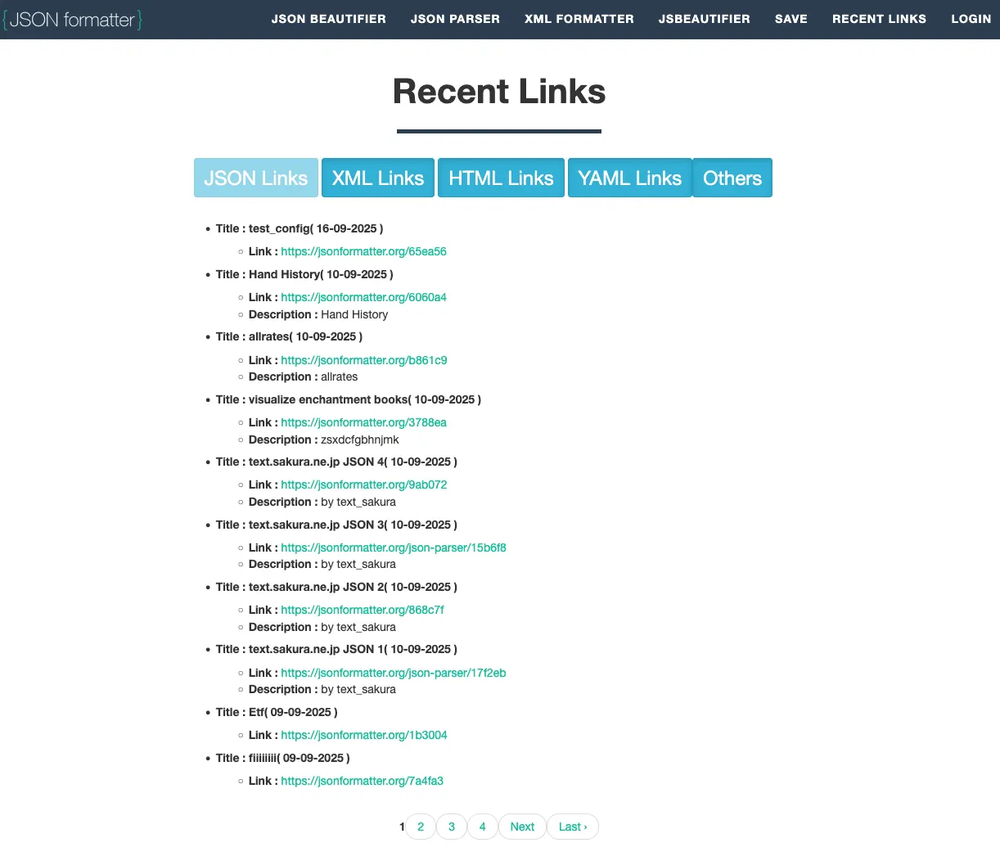
By crawling the “Recent Links” pages and related endpoints on JSONFormatter and CodeBeautify, watchTowr collected more than 80,000 saved JSON submissions over several years.
They then parsed this 5 GB dataset to detect secrets, credentials, and personal data automatically.
The results were alarming: thousands of exposed items, including Active Directory credentials, database passwords, cloud keys, private keys, API tokens, CI/CD credentials, SSH session data, card payment gateway credentials, and extensive PII.
The exposed data did not come solely from small hobby projects.
The researchers found leaks from a wide range of sectors, including critical national infrastructure, government, banking and finance, insurance, technology, cybersecurity vendors, retail, aerospace, telecoms, healthcare, education, and travel.
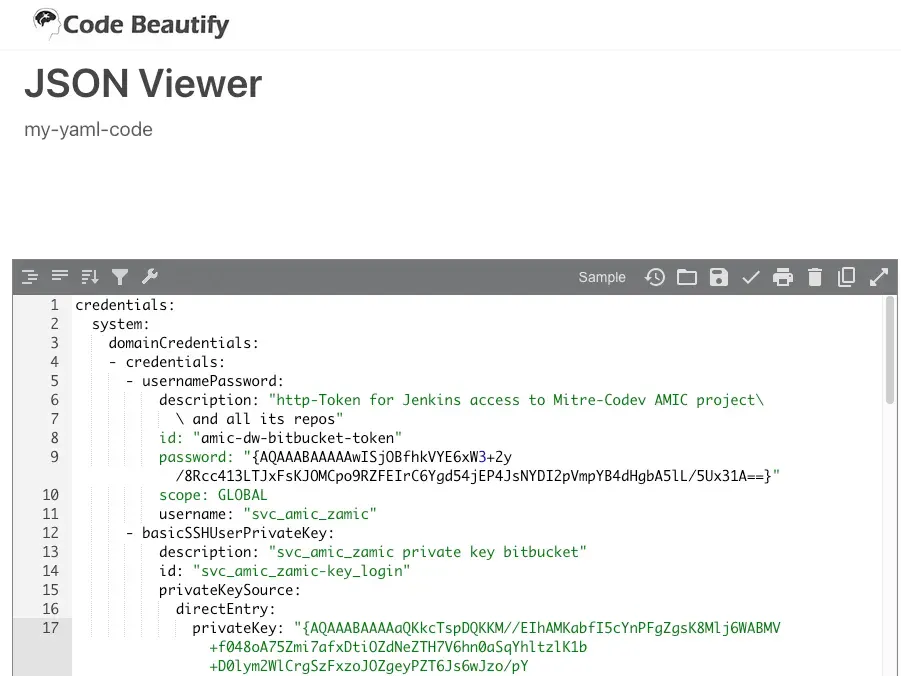
In some cases, entire exports of secrets from tools like AWS Secrets Manager appeared to have been pasted into these services.
Examples highlighted in the research include encrypted Jenkins credentials tied to a MITRE collaboration environment, lengthy PowerShell deployment scripts from a government organisation, and configuration files from a well-known “Datalake-as-a-Service” provider containing Docker, Grafana, JFrog, and database credentials.
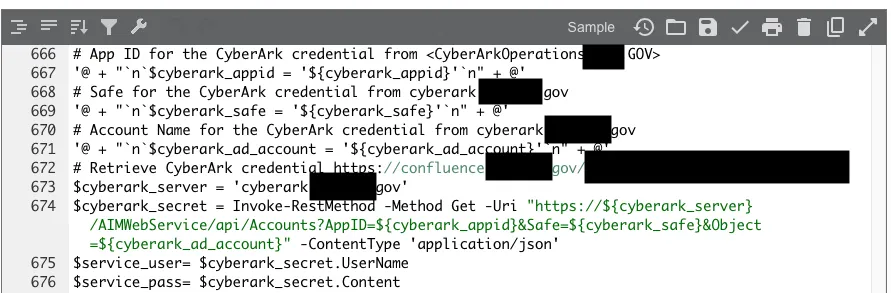
Even a publicly listed cybersecurity company was found to have uploaded encrypted credentials and internal configuration details for sensitive systems.
Beyond credentials, the dataset also contained highly sensitive personal data. In one case, watchTower identified multiple uploads of complete Know Your Customer (KYC) records for a bank in a specific country.
These JSON blobs included names, addresses, emails, usernames, phone numbers, IP addresses, ISPs, and URLs to recorded KYC video interviews hosted on the bank’s domain.
WatchTowr says it worked with national CERTs and notified affected organizations where possible, but response rates were mixed. Many entities did not reply despite multiple contact attempts.
The core issue is not a sophisticated exploit but basic misuse of tools: developers pasting live production data into untrusted third‑party websites and then using “Save” and share links without understanding the exposure.
The incident underscores the need for stricter internal policies, developer training, and safer workflows, such as using offline or self-hosted formatting tools and ensuring that real secrets and PII never leave controlled environments.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
The post Developers Expose Passwords and API Keys via Online Tools like JSONFormatter appeared first on Cyber Security News.



