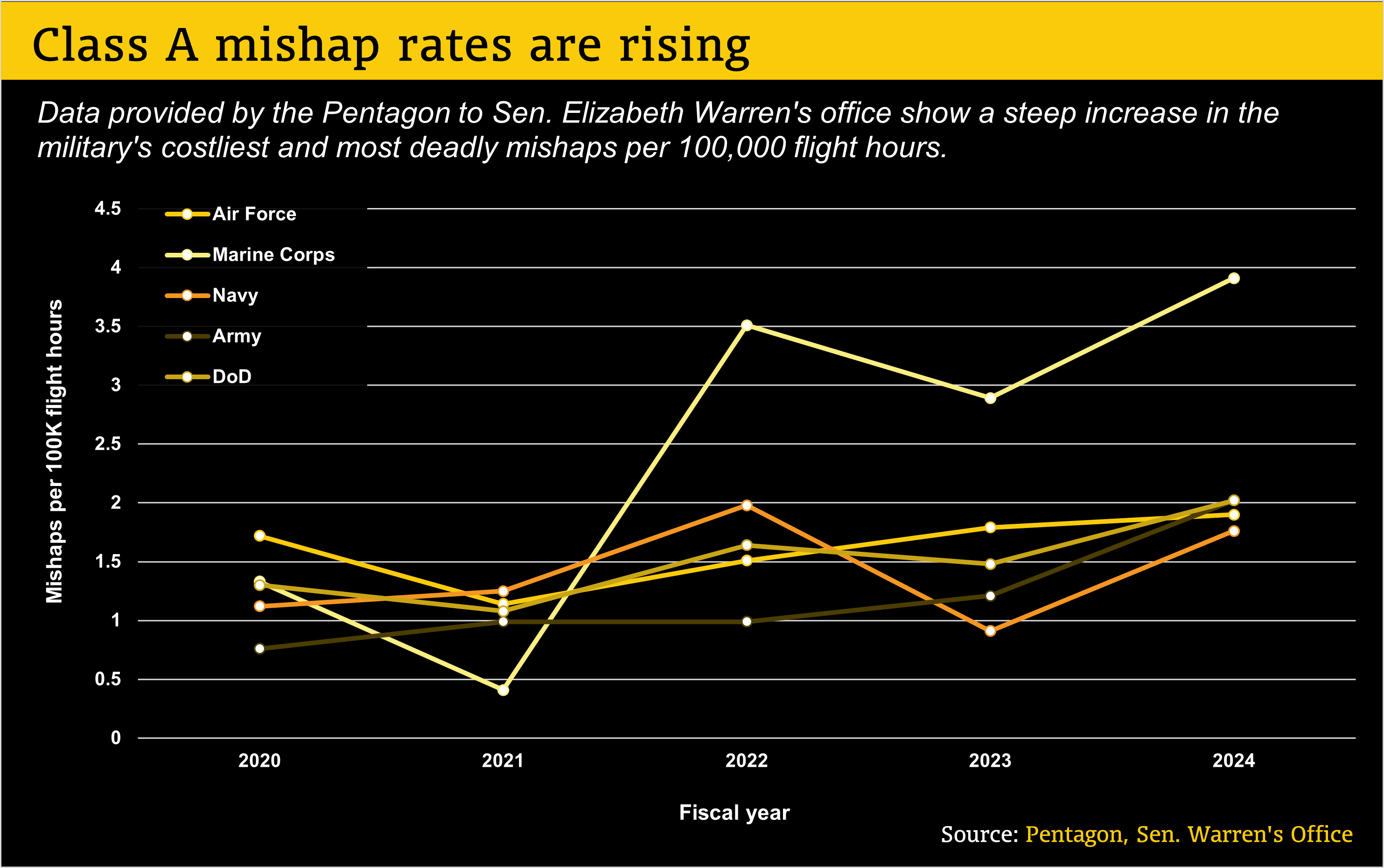
The number of Class A mishaps—the deadliest and costliest category—per 100,000 flight hours rose from 1.3 in fiscal 2020 to 2.02 in fiscal 2024, according to data provided to Sen. Elizabeth Warren, D-Mass. Defense One reviewed the data, which Warren received in January after requesting it last year.
“This loss of life due to mishaps poses an unacceptable risk to service members, their families, and military readiness,” Warren said in a Wednesday news release.
Across 4,280 total mishaps between full budget years 2020 through 2023 and part of 2024, those incidents led to 90 deaths, just shy of 90 aircraft destroyed, and upwards of $9 billion in damages, the data showed.
Warren’s office said the rise in deadly mishaps supports a push to include provisions in this year’s defense policy bill asking the Pentagon to share summaries of internal military safety reports for the last three years with Congress.
Safety advocates and defense experts said the alarming trends are accompanied by declining transparency, increased operations, and stagnating budgets.
Each service except the Navy saw the rate of Class A mishaps per 100,000 flight hours hit a four-year high in 2024. In the Marines, the rate nearly doubled from 1.33 to 3.91. The Army’s rate rose from 0.76 to 2.02; the Air Force’s edged up from 1.72 to 1.9; and the Navy’s went from 1.12 and 1.76 after peaking at 1.98 in 2022.
A Pentagon official, responding to those figures being released by Warren’s office, said in an emailed statement that the Defense Department's safety oversight council regularly reviews incidents to “reduce safety risks” to the services.
"We underscore the importance of safety and readiness at every level of the Department, ensuring that we invest in and adopt leading safety practices and foster a strong culture of safety throughout the organization,” the official said.
The Pentagon data included the Class A mishap rates of its 10 most-used aircraft. The list was topped by the H-60 helicopter, which was involved in 23 total incidents per four years worth of flight hours. It was followed by the F-18 fighter jet and C-17 transport plane, both with 21 total incidents per four years worth of flight hours.
More than one-fifth of the 90 deaths mentioned in the Pentagon report occurred in variants of the V-22 Osprey, which has seen four crashes resulting in 20 servicemember deaths since 2022. One widow who lost a loved one in a 2022 crash said the alarming trend of deadly incidents is made worse by a lack of transparency. Many survivors are still waiting on findings in Naval Air Systems Command and Government Accountability investigations probing the tiltrotor aircraft.
“The trends we’re seeing remain incredibly concerning, and answers aren’t only owed to the families whose loved ones are represented in these numbers. They’re owed to the service members still flying in these aircraft and to their loved ones,” the widow said. “We deserve complete answers and real accountability. We still don’t have either.
Some services, such as the Air Force, have taken public-facing measures addressing the alarming rise in deadly mishaps. Before he retired as Air Force chief of staff earlier this year, then-Gen. David Allvin announced a safety and standards campaign in January, stating in a video the service lost 47 airmen and $1.5 billion in weapons due to preventable incidents. His replacement, Gen. David Wilsbach, told Congress during his confirmation hearing, and airmen in a letter this month, that his priority is to fix aging aircraft and increase readiness.
J.F. Joseph, a retired Marine Corps pilot who is an aviation consultant and expert witness, said reversing the trends will require pilots to get enough flight hours. That involves consistently funding and staffing maintenance efforts so aviators can get more experience.
“The aircraft have to be supported by the maintainers and they have to have the parts, the components, to maintain those aircraft properly,” Joseph said. “If you don’t staff these aircraft squadrons properly with maintainers, even if you have the parts sitting on the shelf, you can’t fix the airplanes. The cost of doing aviation safely is expensive, it simply is. It’s even more expensive when you’re doing it properly, but it’s a lot more expensive when you’re not.”
This year alone, the Navy lost four F/A-18Fs, according to Warren’s office, and the deadliest mishap in recent aviation history took place near Washington, D.C., in January when an Army Black Hawk helicopter collided in midair with a commercial airliner, killing all 67 aboard the two aircraft.
Mackenzie Eaglen, a senior fellow at the American Enterprise Institute, said prior administrations’ defense budgets “did not keep pace with inflation while the military op-tempo was high,” adding that several services have had to take drastic measures to keep aircraft usable–such as the Air Force resurrecting retired B-1 Lancer bombers and returning them to service.
“Shockingly, military aviation units in separate branches in the armed services are currently cannibalizing aircraft parts to get planes flying,” Eaglen said. “The decade-long budget control act, followed by sequestration, followed by budgets that did not keep pace with generational record-high inflation mean there is a lot of time, work, and money needed to reverse these trends.”
In a Tuesday letter to Defense Secretary Pete Hegseth, Warren’s office is now asking for Class A-mishap data for the rest of 2024 and 2025 as well as broader information on “mishaps, fatalities, destroyed aircraft, and estimated costs across each service for each aircraft” in the past five years. The senator asked for the Pentagon to provide the information no later than Dec. 2.
“In the face of increasing rates of costly and deadly aviation mishaps, it is critical that Congress and DoD take all necessary action to address this problem,” Warren wrote.
]]>





