-
The exploitation of a recently disclosed critical security flaw in Motex Lanscope Endpoint Manager has been attributed to a cyber espionage group known as Tick. The vulnerability, tracked as CVE-2025-61932 (CVSS score: 9.3), allows remote attackers to execute arbitrary commands with SYSTEM privileges on on-premise versions of the program. JPCERT/CC, in an alert issued this month, said that it
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Google has announced enhanced artificial intelligence protections designed to combat the rising tide of mobile scams affecting billions of users worldwide. The company revealed that fraudsters stole over $400 billion globally in the past year using advanced AI-powered schemes, making mobile security more critical than ever. Android’s Advanced Defense Against Mobile Fraud Google’s Android platform […]
The post Google Launches New AI Security Features on Android to Block Mobile Scams appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Progress Software has released critical security patches addressing a high-severity vulnerability affecting MOVEit Transfer, a widely used enterprise file transfer solution.
The vulnerability, tracked as CVE-2025-10932, carries a CVSS score of 8.2 and impacts the AS2 module across multiple product versions.
The uncontrolled resource consumption vulnerability in MOVEit Transfer’s AS2 module could allow attackers to disrupt service availability by exhausting system resources.
The flaw exists in versions 2025.0.0 through 2025.0.2, 2024.1.0 through 2024.1.6, and 2023.1.0 through 2023.1.15. With a network-accessible attack vector requiring no authentication or user interaction, organizations using affected versions face significant exposure to potential service disruptions and exploitation.
MOVEit Transfer Vulnerability
The vulnerability stems from inadequate controls over resource consumption, classified under CWE-400. This category of flaws enables attackers to overwhelm systems by forcing excessive resource allocation, leading to denial-of-service conditions that impact legitimate business operations.
Progress has distributed hotfixes that mandate IP address whitelisting for the AS2 module, creating a protective barrier against unauthorized access. Organizations must take immediate action based on their specific deployment model.
For enterprises not utilizing the AS2 module with MOVEit products, a temporary workaround involves removing the vulnerable endpoints.
Administrators should delete the AS2Rec2.ashx and AS2Receiver.aspx files from the C:\MOVEitTransfer\wwwroot directory. This straightforward approach requires no server restart and maintains continuity until permanent patches are applied.
For organizations actively using AS2 functionality, applying the hotfix becomes essential. After updating to the patched versions MOVEit Transfer 2025.0.3, 2024.1.7, or 2023.1.16, administrators must configure IP whitelist rules for authorized trading partners.
Attribute Value CVE ID CVE-2025-10932 Product Progress MOVEit Transfer Vulnerability Type Uncontrolled Resource Consumption Affected Module AS2 Module CVSS Score 8.2 (HIGH) This involves logging into MOVEit Transfer as an administrator, navigating to Settings, accessing Security Policies, and configuring Remote Access Rules to restrict AS2 module access to trusted partner IP addresses.
Progress has made fixed versions available through its Download Center for customers maintaining current maintenance agreements. The patch availability spans three major version lines, ensuring organizations can update within their supported product branch.
Customers without active maintenance agreements should contact Progress renewal services or their designated partner account representative.
Notably, Progress MOVEit Cloud users require no immediate action, as the cloud infrastructure has already been upgraded to patched versions. However, on-premises deployments demand rapid attention to mitigate exposure.
Organizations running MOVEit Transfer versions outside these active branches should prioritize upgrading to currently supported releases or implementing the temporary AS2 endpoint removal workaround.
The high CVSS score reflects the severity of this vulnerability and the potential business impact of service disruptions. Quick deployment of patches represents a critical priority for security teams managing file transfer infrastructure across their enterprise environments.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
The post Progress Patches MOVEit Transfer Uncontrolled Resource Consumption Vulnerability appeared first on Cyber Security News.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
HONOLULU—No single technology can win every battle and fix every problem, the leader of Special Operations Command Pacific said this week. Instead, the “ability to integrate multiple systems, disparate systems, with more open architecture—that is eventually going to win. If you have that sort of single, standalone technology…it’s likely to be cracked, hacked, and eventually overcome.”
Remember the Karate Kid movies, Maj. Gen. Jeffrey VanAntwerp urged his audience at the AFCEA TechNet Indo-Pacific conference here. When Daniel learned a crane kick, Mr. Miyagi told him, “If done right, no can defense,” VanAntwerp said. “And that worked in Karate Kid one, but then in Karate Kid two, he goes to Okinawa, to people who are more familiar with the operational environment, and…the crane kick did not work.…He eventually had to go to the spinning drum.”
For SOCPAC, VanAntwerp said the combination of robotics, autonomy, and resilient networks is “absolutely critical,” because information is useless unless it comes with an ability to make a coherent picture. And whatever combination of systems that might emerge, having “the ability to disrupt our adversaries’ ability to target us, that is the oxygen that we require in this theater.”
VanAntwerp recounted a Ukrainian SOF commander’s remarks at a recent forum, noting that Ukraine has been able to deny Russia access to large portions of the Black Sea without a navy, deny air superiority with no air force, and hold the line with a significantly smaller army.
“They’ve been able to do that through a combination of the ability to see and sense and understand… with some help from partners,” and a network of various unmanned systems, he said. “It’s pretty amazing, and provides a really great example for us.”
So why is it taking the United States so much longer to adapt? VanAntwerp believes the key reason is “the lack of a tactical imperative”—namely, no American troops are dying on battlefields.
“I do believe this machine, which includes all of you and us, can move incredibly fast when there is that imperative,” he told the audience of industry representatives and troops. “But without it, we tend to, knowingly or unknowingly, we tend to pace ourselves.”
And as officials consider solutions, VanAntwerp said they must also be careful to consider the “cost curve,” he said.
With unmanned systems and the networks that enable them, the goal is to either have expendable low cost systems, or expensive highly survivable systems. “If we get caught in the middle, which is where we often find ourselves… that’s just bankruptcy. We can’t afford it.”
]]>¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Throughout the first half of 2025, the FortiGuard Incident Response team investigated dozens of security breaches across multiple industries driven by financially motivated threat actors. What emerged from these investigations was a striking pattern: attackers are abandoning complex, malware-heavy approaches in favor of a deceptively simple method—simply logging in using stolen credentials and leveraging legitimate […]
The post Stolen Credentials Drive the Rise of Financially Motivated Cyberattacks appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Microsoft has launched Researcher with Computer Use in Microsoft 365 Copilot, marking a significant advancement in autonomous AI technology. This new feature allows the AI assistant to move beyond simple research tasks and actively perform actions on behalf of users through a secure virtual computer environment.
The innovation enables Copilot to navigate public websites, access authenticated content, and interact with web pages while maintaining enterprise-level security standards.
The Computer Use feature empowers Researcher to access premium subscription-based content that requires login credentials, execute tasks by clicking buttons and filling forms, and generate complex outputs such as presentations and spreadsheets.
The system operates through a virtual machine running on Windows 365, which functions as a temporary cloud-based computer dedicated to each conversation session.
How Computer Use Transforms Research Capabilities
Users can request Researcher to prepare customer meeting briefs by gathering social media insights, create personalized reading lists based on ongoing projects, analyze industry trends from gated publications, or transform research findings into polished presentations.
The technology connects to work data, including meetings, files, and chats, while providing users full visibility and control.
When activated, Researcher utilizes visual browsers, text browsers, terminal interfaces, and Microsoft Graph to execute comprehensive workflows.
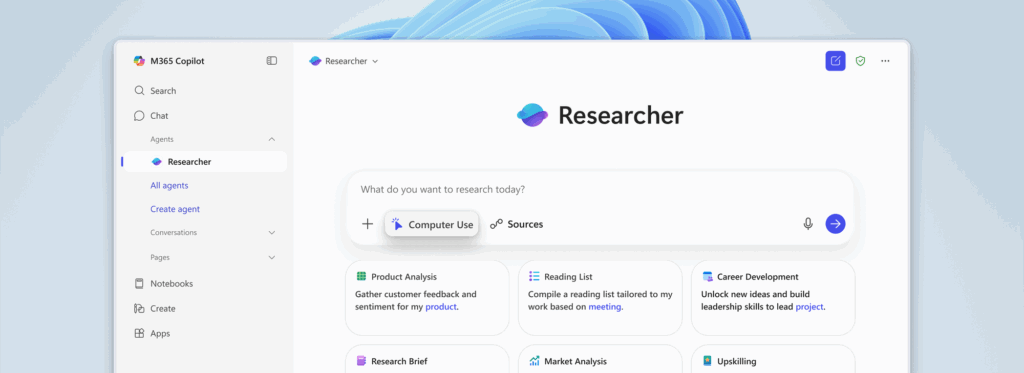
Researcher with Computer Use Users can customize which data sources the system accesses, and enterprise data remains disabled by default when Computer Use is activated.
The system requests explicit user confirmation before taking actions and allows users to take control through secure screen-sharing when authentication is required.
Microsoft has implemented robust security measures to address potential risks associated with autonomous AI operations. The virtual machine operates in a fully sandboxed environment, isolated from corporate networks and user devices.
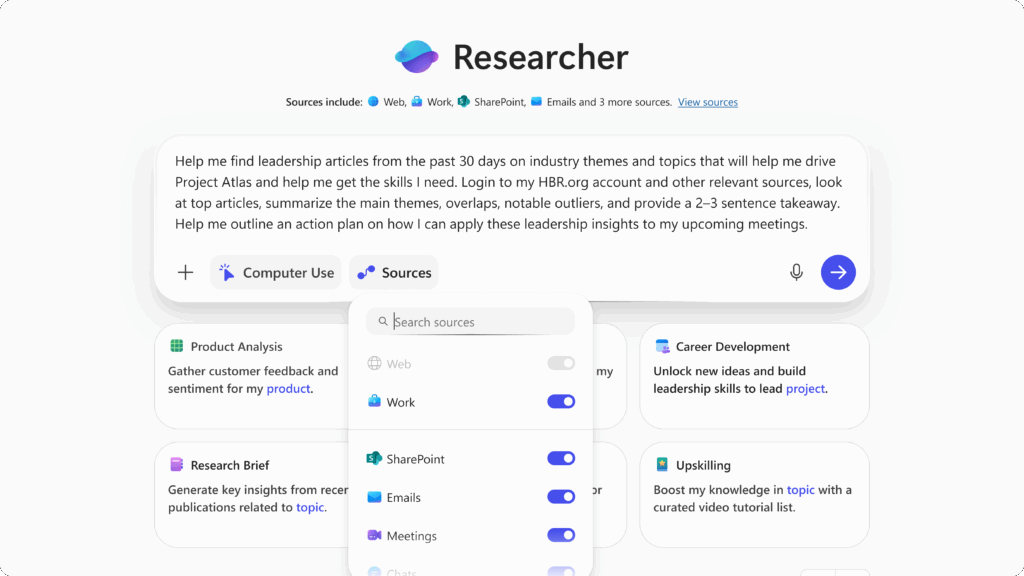
Users can choose to enable the set of work data sources Safety classifiers inspect every network operation to validate domain safety, verify relevance to user queries, and analyze content types. This protection helps prevent cross-prompt injection attacks and jailbreak attempts that might occur during web navigation.
Browser actions performed in the sandbox are fully auditable through standard Microsoft 365 Copilot logging mechanisms.
User credentials never transfer to or from the sandbox environment, and all intermediate files are automatically deleted when sessions end.
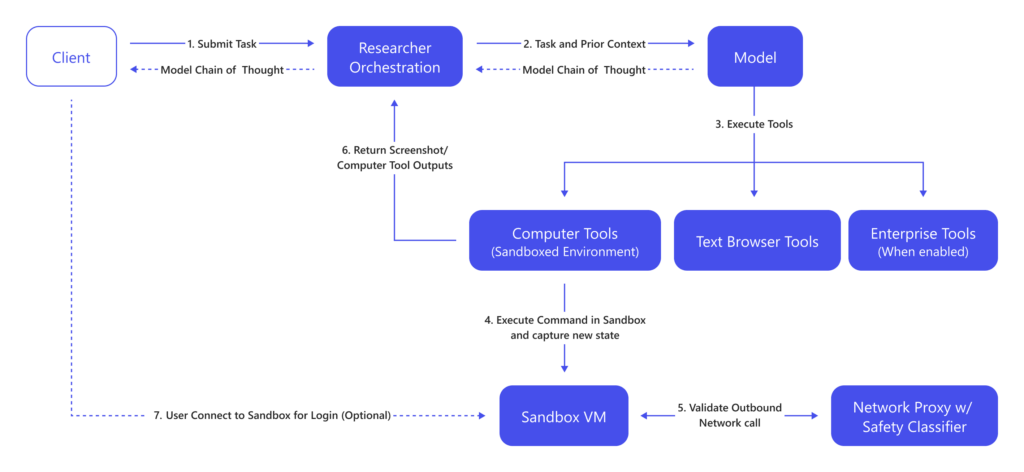
The orchestration layer connects to a sandbox environment Administrators control feature availability through the Microsoft Admin Center, where they can specify which security groups can access Computer Use, manage domain allow and deny lists, and govern whether users can combine enterprise and web data.
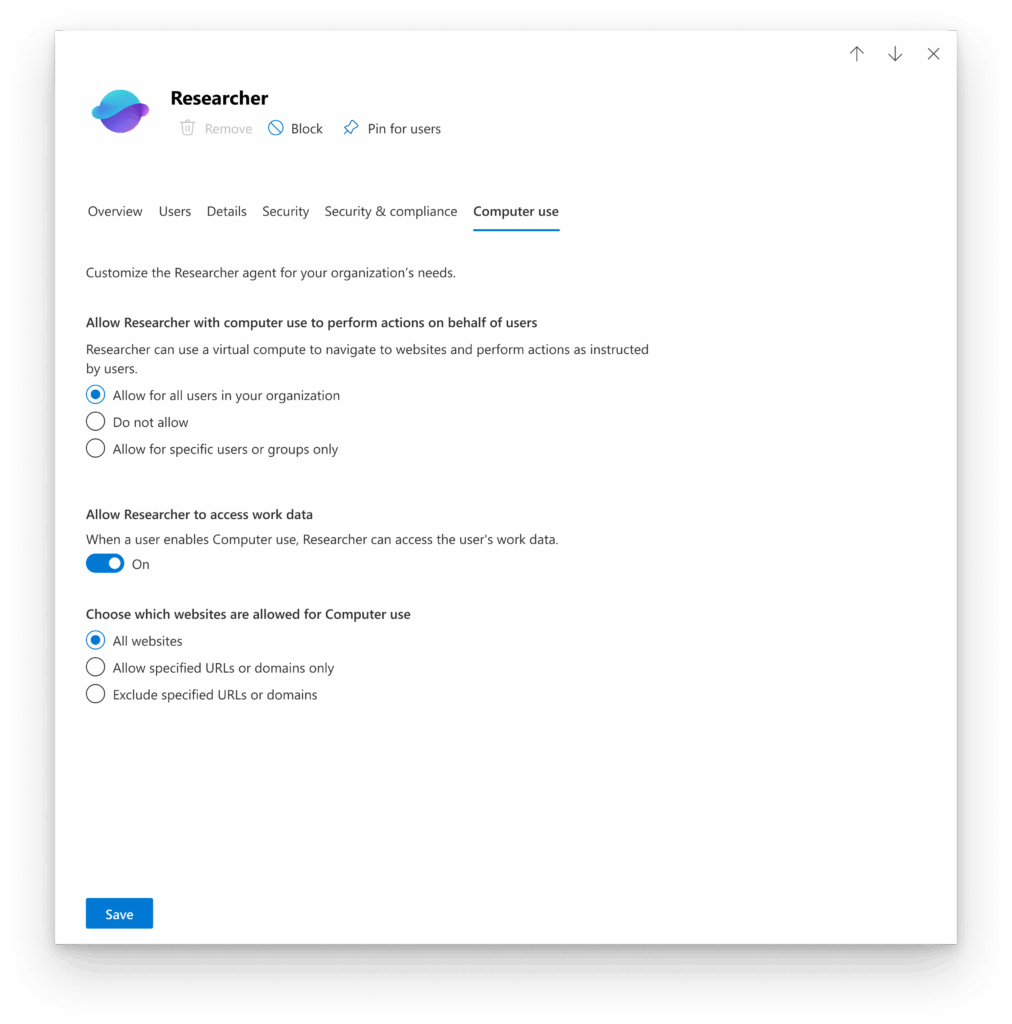
Admin Controls Performance testing demonstrates substantial improvements, with Researcher achieving 44% better results on BrowseComp benchmarks for complex browsing tasks and 6% improvement on GAIA evaluations.
These benchmarks measure the system’s ability to reason across multiple information sources, synthesize scattered data, and solve real-world research challenges that require accessing diverse datasets and corporate records.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
The post Microsoft Introduces Researcher in 365 Copilot: Your Secure Virtual Assistant for Enhanced Productivity appeared first on Cyber Security News.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
The proliferation of artificial intelligence applications has created unprecedented opportunities for cybercriminals to exploit user trust through deceptive mobile apps. Mobile app stores today are flooded with hundreds of lookalike applications claiming to offer ChatGPT, DALL·E, and other AI services. Security researchers have discovered that beneath polished logos and promises of advanced functionality lies a […]
The post Beware of Fake ChatGPT Apps That Spy on Users and Steal Sensitive Data appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
The Cybersecurity and Infrastructure Security Agency (CISA) has added a critical vulnerability affecting XWiki Platform to its Known Exploited Vulnerabilities catalog, highlighting the urgent security threat posed by an eval injection flaw. This vulnerability could allow any guest user to execute arbitrary remote code without authentication, representing a severe risk to organizations using the popular […]
The post CISA Issues Advisory on XWiki Flaw Allowing Remote Code Execution appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
MSPs are facing rising client expectations for strong cybersecurity and compliance outcomes, while threats grow more complex and regulatory demands evolve. Meanwhile, clients are increasingly seeking comprehensive protection without taking on the burden of managing security themselves. This shift represents a major growth opportunity. By delivering advanced cybersecurity and compliance
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In mid-2025, Secureworks Counter Threat Unit (CTU) researchers uncovered a sophisticated cyber campaign where Chinese state-sponsored threat actors from the BRONZE BUTLER group exploited a critical zero-day vulnerability in Motex LANSCOPE Endpoint Manager to gain unauthorized access to corporate networks and extract sensitive data. The discovery marks another chapter in a long-running pattern of exploitation […]
The post Threat Actors Exploit LANSCOPE Endpoint Manager Zero-Day Vulnerability to Steal Confidential Data appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶


