BreachLock, the global leader in Penetration Testing as a Service (PTaaS), has been recognized as a Representative Provider in the 2025 Innovation Insight: Penetration Testing as a Service report by Gartner.
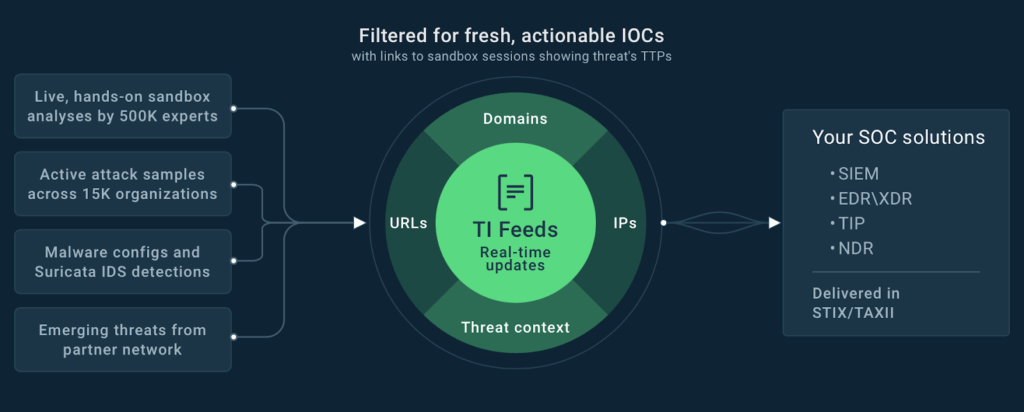
The report highlights how PTaaS helps organizations increase testing frequency by automating routine tasks, supports compliance objectives with high-level standardization and customizable reporting, and helps reduce exposure by closely supporting continuous threat exposure management (CTEM) strategies, enabling organizations to remediate emerging risks faster.
This latest recognition from Gartner –– following multiple other recognitions from Gartner this year for PTaaS, Adversarial Exposure Validation (AEV), and CTEM –– underscores BreachLock’s commitment to delivering more scalable, flexible, and efficient penetration testing solutions for modern security teams.
“Static or periodic penetration testing simply can’t defend dynamic attack surfaces anymore. Gartner’s recognition of PTaaS reinforces what our clients experience daily — offensive security needs to be agentic, adaptive, and continuous,” stated Seemant Sehgal, Founder & CEO of BreachLock. “Our Agentic Offensive Security solution autonomously discovers, prioritizes, and validates exposures in real time — turning Pen Testing from a reactive process into a living, self-optimizing defense mechanism.”
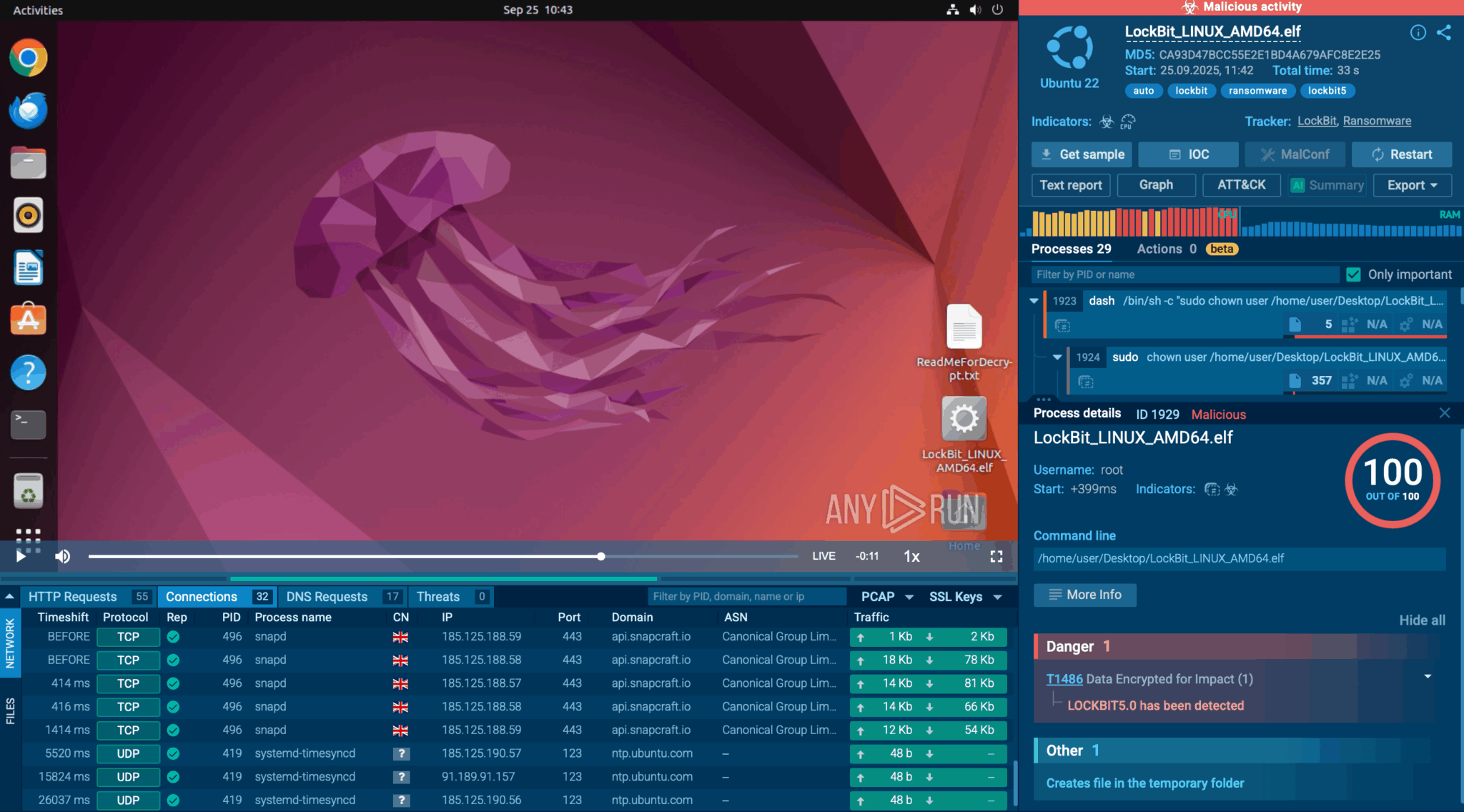
BreachLock PTaaS blends human expertise, AI, and automation to help security teams identify, prioritize, and remediate risk not only faster, but continuously. The company offers flexible and versatile managed-service, self-service, and hybrid PTaaS solutions, enabling customers to test what they want, when they want, as frequently as they want, whether that’s periodically, continuously, or on demand.
BreachLock makes penetration testing fast and scalable, and enables smarter vulnerability prioritization with deeper, AI-contextualized insights that go beyond CVSS risk scoring, accounting for business context and leveraging historical data from thousands of pentests.
Delivered through the BreachLock Unified Platform, PTaaS integrates seamlessly with the company’s adjacent offensive security solutions, including Adversarial Exposure Validation (AEV), its generative AI-powered autonomous red teaming engine, and Attack Surface Management (ASM). Together, these solutions form a unified foundation for continuous discovery, validation, prioritization, and remediation in alignment with enterprise CTEM programs.
About BreachLock
BreachLock is a global leader in offensive security, delivering scalable and continuous security testing. Trusted by global enterprises, BreachLock provides human-led and AI-powered Attack Surface Management, Penetration Testing as a Service (PTaaS), Red Teaming, and Adversarial Exposure Validation (AEV) solutions that help security teams stay ahead of adversaries.
With a mission to make proactive security the new standard, BreachLock is shaping the future of cybersecurity through automation, data-driven intelligence, and expert-driven execution.
Disclaimer
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Contact
Senior Marketing Executive
Megan Charrois
BreachLock
megan.c@breachlock.com
The post BreachLock Named Representative Provider for Penetration Testing as a Service (PTaaS) in New Gartner® Report appeared first on Cyber Security News.