A widespread campaign observed exploiting a novel zero-day vulnerability in Oracle E-Business Suite (EBS) applications, now tracked as CVE-2025-61882.
First observed on August 9, 2025, this unauthenticated remote code execution (RCE) flaw is being weaponized to bypass authentication, deploy web shells, and exfiltrate sensitive data from internet-exposed EBS instances.
CrowdStrike assesses with moderate confidence that the threat actor GRACEFUL SPIDER is behind the mass exploitation, although evidence suggests additional actors may be involved.
Mass Exploitation Campaign
On September 29, 2025, GRACEFUL SPIDER allegedly sent Clop-branded emails to multiple organizations claiming successful data theft from Oracle EBS applications.
Shortly after the October 3, 2025 proof-of-concept (POC) disclosure and Oracle’s patch release, a Telegram channel post hinted at collaboration between SCATTERED SPIDER, SLIPPY SPIDER, and the ShinyHunters group.
The post included a purported EBS exploit with SHA256 hash 76b6d36e04e367a2334c445b51e1ecce97e4c614e88dfb4f72b104ca0f31235d and criticized GRACEFUL SPIDER’s tactics.
Oracle’s advisory incorporated this PoC as an indicator of compromise (IOC), implying vendor concerns over in-the-wild exploitation.
CrowdStrike connects activity leveraging Java Servlets for initial compromise, indicating the POC aligns closely with observed intrusions.
Despite ongoing investigation into the exploit’s provenance and distribution, the timing of public POC release and patch deployment is likely to spur further weaponization by adversaries familiar with Oracle EBS.
The exploit begins with an HTTP POST request to /OA_HTML/SyncServlet, triggering the authentication bypass. Confirmed incidents show adversaries leveraging administrative account privileges within EBS.
Following bypass, attackers target the XML Publisher Template Manager via GET /OA_HTML/RF.jsp and POST /OA_HTML/OA.jsp to upload a malicious XSLT template.
Commands embedded in the template execute upon preview, which captures sample GET and POST requests used to upload and preview the payload.
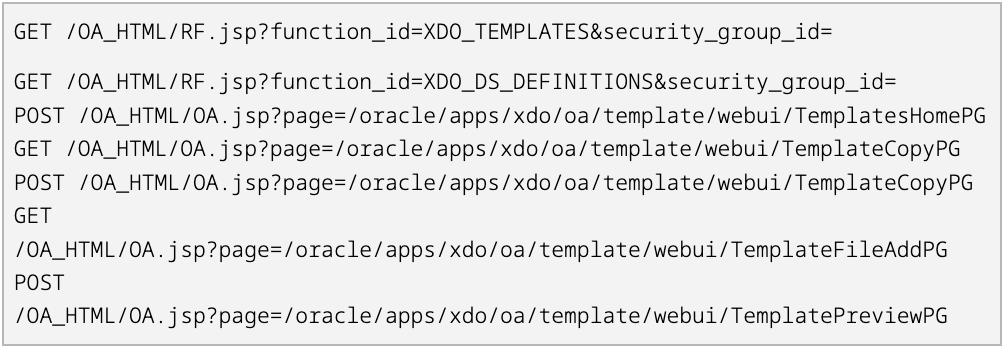
Template names retrieved from the xdo_templates_vl view correspond to TemplateCode URL references.

Successful template execution establishes an outbound Java process connection over port 443 to the attacker-controlled infrastructure.
Analysis indicates this channel is used to load web shells, often via a two-step process: loading FileUtils.java to download a secondary backdoor Log4jConfigQpgsubFilter.java.
The backdoor engages through a doFilter chain at the public endpoint /OA_HTML/help/state/content/destination./navId.1/navvSetId.iHelp/, enabling command execution and persistence.
CrowdStrike Intelligence emphasizes that CVE-2025-61882 presents a significant remote code execution (RCE) risk to Oracle EBS environments.
Organizations are urged to apply the October 4, 2025, patch immediately, audit outbound connections for suspicious activity, review xdo_templates_vl for unauthorized templates, investigate icx_sessions for UserID 0 and UserID 6 anomalies, and deploy web application firewalls to protect exposed EBS services.
Monitoring for Java process behaviors consistent with published Falcon LogScale and SIEM detection rules can further mitigate ongoing exploitation risks.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today
The post CrowdStrike Warns of New Mass Exploitation Campaign Leveraging Oracle E-Business Suite 0-Day appeared first on Cyber Security News.



.webp)
