-
Unknown threat actors are abusing Milesight industrial cellular routers to send SMS messages as part of a smishing campaign targeting users in European countries since at least February 2022. French cybersecurity company SEKOIA said the attackers are exploiting the cellular router’s API to send malicious SMS messages containing phishing URLs, with the campaigns primarily targeting Sweden, Italy,
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A novel rootkit hooking method dubbed FlipSwitch has emerged, circumventing the latest Linux 6.9 kernel dispatch safeguards and reigniting concerns over kernel-level compromise. By manipulating the machine code of the new syscall dispatcher rather than the deprecated sys_call_table, FlipSwitch restores the classic power of syscall hooking, enabling stealthy interception of critical system calls such as […]
The post New FlipSwitch Hooking Method Overcomes Linux Kernel Defenses appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Red Hat published security advisory CVE-2025-10725, detailing an Important severity flaw in the OpenShift AI Service that could enable low-privileged attackers to elevate their permissions to full cluster administrator and compromise the entire platform.
With a CVSS v3 base score of 9.9, this vulnerability poses a critical risk for organizations leveraging Red Hat OpenShift AI for machine learning workloads.
Privilege Escalation Vulnerability (CVE-2025-10725)
The root cause of CVE-2025-10725 lies in an overly permissive ClusterRoleBinding associating the kueue-batch-user-role with the system:authenticated group.
In typical deployments, data scientists and other authenticated users access Jupyter notebooks and AI pipeline features with minimal privileges.
However, by exploiting this misconfiguration, an attacker can invoke the batch.kueue.openshift.io API to create arbitrary Job and Pod resources.
Inject malicious containers or init-containers that execute oc or kubectl commands, chain privilege elevation within the cluster by binding newly created service accounts to higher-privilege roles.
Ultimately, assume the cluster-admin role and gain unrestricted read/write access to all cluster objects. This exploit completely undermines the confidentiality, integrity, and availability of hosted workloads, allowing theft of sensitive data, service disruption, and full infrastructure takeover.
Risk Factors Details Affected Products Red Hat OpenShift AI 2.19 (RHEL 8)Red Hat OpenShift AI 2.21 (RHEL 9)registry.redhat.io/rhoai/odh-rhel8-operatorregistry.redhat.io/rhoai/odh-rhel9-operator Impact Privilege escalation Exploit Prerequisites Valid authenticated user accountAccess to OpenShift AI ServiceLow-privileged account, Access to Jupyter notebook or similar interface, Ability to interact with batch.kueue.openshift.io API CVSS 3.1 Score 9.9 (Critical) Mitigations
Red Hat has released fixes in the following errata, updating the OpenShift AI Operator for Red Hat Enterprise Linux 8 and 9:
- RHBA-2025:16984 (OpenShift AI 2.19 on RHEL 8)
- RHBA-2025:16983 (OpenShift AI 2.21 on RHEL 9)
Administrators should apply these updates immediately. As a workaround before patching, remove the problematic ClusterRoleBinding:
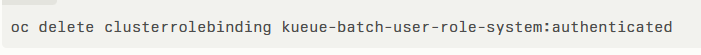
Then, grant job-creation permissions explicitly to trusted identities. This approach enforces the Principle of Least Privilege, ensuring only designated users or groups can submit AI jobs.
Red Hat classifies CVE-2025-10725 as Important rather than Critical because the attacker must hold a valid authenticated account, albeit with low privileges.
Nonetheless, the impact remains severe. Organizations running Red Hat OpenShift AI should remediate promptly to prevent complete cluster compromise and adhere to hardened RBAC configurations going forward.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
The post Red Hat Openshift AI Service Vulnerability Allow Attackers to Take Control of the Infrastructure appeared first on Cyber Security News.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Confidential computing promised to protect sensitive workloads in the public cloud. Yet a new low-cost hardware attack, Battering RAM, demonstrates that even up-to-date memory-encryption schemes on Intel and AMD processors can be defeated with a simple interposer costing under 50 dollars.
Modern servers use DDR4 DRAM with hardware-backed encryption, such as Intel SGX’s Total Memory Encryption (TME) and AMD SEV-SNP, to guard private data.
Previous research on “BadRAM” exploited false SPD metadata at boot time; in response, vendors implemented stricter boot-time alias checks.
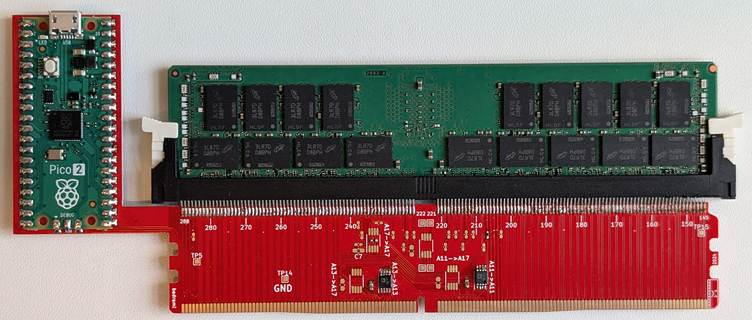
Building Battering RAM on $50 Budget Battering RAM Attack
Battering RAM operates dynamically, where a custom interposer sits between the CPU and DIMM, transparent during POST, and evades SPD spoofing checks.
Once the system is online, an analog switch flips, redirecting encrypted traffic from victim addresses to an attacker-controlled alias buffer.
Captured ciphertext is then replayed into a controlled enclave, yielding arbitrary plaintext access. This attack fully compromises both SGX and SEV-SNP attestation on patched cloud platforms, enabling read/write of enclave memory.
The interposer design, shared on GitHub, uses two SPDT analog switches and a microcontroller to toggle aliasing at runtime.
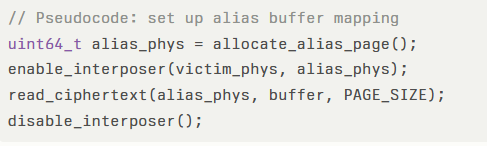
This code fragment illustrates the two-phase capture-and-replay process that yields decrypted enclave data.
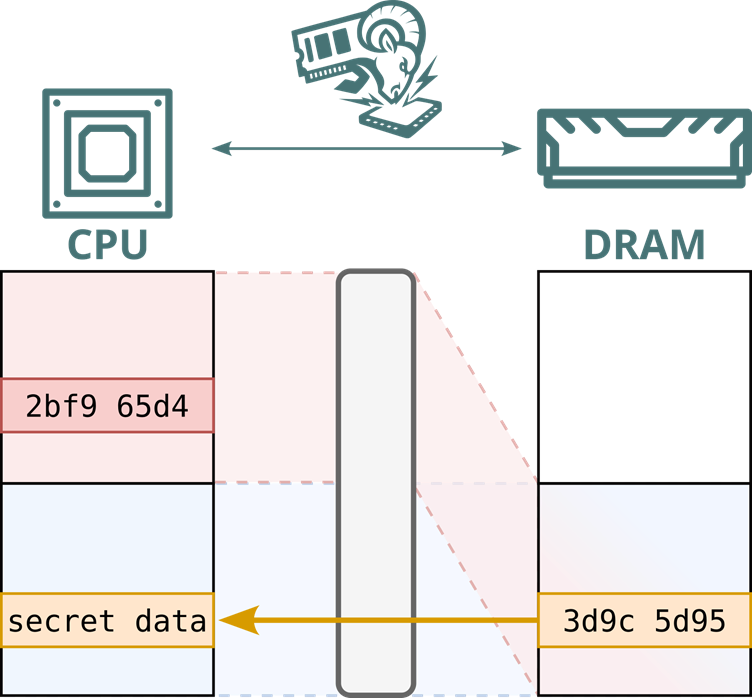
Battering RAM Attack Implications for Cloud Security
Battering RAM exposes fundamental flaws in static memory-encryption engines, which lack cryptographic freshness checks.
Because TME and SEV-SNP derive ciphertext solely from a fixed key and physical address, replayed data decrypts predictably, nullifying passive-attack defenses like cold-boot mitigation.
Key implications include:
- Physical-layer adversaries rogue cloud staff or supply-chain attackers require only brief access to install the interposer.
- Software or firmware patches cannot detect on-the-fly address remapping. True mitigation demands per-page nonce or integrity checks integrated into the DRAM encryption engine.
- At under $50, Battering RAM democratizes a class of attacks formerly limited to high-end DRAM interposers (> $100,000).
Academic teams at KU Leuven, University of Birmingham, and Durham University conducted the research and have published schematics, firmware, and proof-of-concept code under CC0.
Both Intel and AMD have issued security advisories acknowledging the findings, but note that physical interposer attacks are beyond the current product scope.
As public cloud adoption of SGX and SEV-SNP grows, covering services on AWS, Azure, Google Cloud, and IBM Cloud, organizations must reassess the physical security of datacenter infrastructure.
Without significant enhancements to memory encryption protocols, Battling RAM underscores that confidential computing is not indestructible.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
The post New Battering RAM Attack Bypasses Latest Defenses on Intel and AMD Cloud Processors appeared first on Cyber Security News.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Detour Dog, a stealthy website malware campaign tracked since August 2023, has evolved from redirecting victims to tech-support scams into a sophisticated DNS-based command-and-control (C2) distribution system that delivers the Strela Stealer information stealer via DNS TXT records. Tens of thousands of compromised websites worldwide make server-side DNS requests that are invisible to visitors, enabling […]
The post New DNS Malware ‘Detour Dog’ Uses TXT Records to Deliver Strela Stealer appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In recent weeks, security teams worldwide have observed a surge in covert operations orchestrated by a clandestine group known colloquially as the “Chinese Nexus” APT.
This actor has been tailoring highly targeted campaigns against organizations in the finance, telecommunication, and manufacturing sectors, exploiting spear-phishing emails and compromised VPN credentials to gain initial footholds.
Victims report receiving seemingly innocuous industry whitepapers with weaponized macros that, once enabled, unleash a payload designed to deliver the NET-STAR malware suite.
Early telemetry indicates that these lures have achieved a success rate of approximately 30 percent against high-value targets.
Following intrusion, the attackers employ living-off-the-land techniques, invoking Windows PowerShell to execute obfuscated scripts directly in memory.
Palo Alto Networks researchers identified that the initial PowerShell stager decodes a Base64 string, reconstructs a .NET binary, and then dynamically injects it into a legitimate process such as explorer.exe or svchost.exe to evade detection.
This process unfolds within seconds of macro activation, leaving scant forensic artifacts on disk. The stealthy nature of the loader has complicated triage efforts, allowing the adversary to proceed to reconnaissance and lateral movement undetected.
Once deployed, NET-STAR exhibits a modular design composed of three primary components: the loader, the backdoor, and the command-and-control (C2) communication module.
The loader’s primary responsibility is to decrypt and load the backdoor payload into memory. The backdoor itself provides a robust set of remote administration capabilities, including file transfer, process manipulation, and registry modification.
Finally, the C2 module establishes an encrypted HTTPS tunnel to a rotating list of compromised web servers.
Analysts observed that each communication session employs a custom framing protocol with 256-bit AES encryption, thwarting standard network-based intrusion detection systems.
In its initial wave of infections, NET-STAR has been linked to exfiltration of proprietary data, ranging from financial records to intellectual property.
Impact assessments indicate that the adversary’s goal extends beyond espionage, aiming to position implants for future sabotage or secondary payload deployment.
.webp)
The maturation process of Phantom Taurus (Source – Palo Alto Networks) Incident responders have noted indicators of credential harvesting via in-memory Mimikatz execution, followed by lateral movement through SMB and RDP channels.
Affected organizations have reported operational disruption and data loss, underscoring the criticality of rapid detection and containment measures.
Infection Mechanism
A deep dive into NET-STAR’s infection mechanism reveals a sophisticated multi-stage process that begins with a malicious Word document. The embedded VBA macro (see Figure 1: “macro_decoder.png”) contains the following snippet:
$enc = "U3lzdGVtLkNvbnZlcnQuQ29tcHJlc3Npb24=" $bytes = [Convert]::FromBase64String($enc) $asm = [Reflection.Assembly]::Load($bytes) $method = $asm.GetType("Loader.Main").GetMethod("Execute") $method.Invoke($null,$null)This code decodes a Base64-encoded .NET assembly and invokes its entry point entirely in memory, leaving no executable on disk.
Palo Alto Networks analysts noted that the loader further employs Control Flow Flattening, obfuscating the assembly’s intermediate language to resist decompilation and prevent signature-based detection mechanisms.
Once loaded into a trusted process, the backdoor receives a second stage payload via HTTPS from the C2, completing the infection and solidifying persistence.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.
The post New Chinese Nexus APT Hackers Attacking Organizations to Deliver NET-STAR Malware Suite appeared first on Cyber Security News.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A sophisticated phishing campaign has emerged targeting job seekers through fake Google career recruitment opportunities, leveraging social engineering tactics to harvest Gmail credentials and personal information.
The malicious operation exploits the trust associated with Google’s brand reputation, crafting convincing recruitment emails that direct victims to fraudulent login portals designed to capture authentication details.
The attack vector primarily relies on email-based social engineering, where cybercriminals impersonate Google HR representatives offering lucrative career opportunities.
These deceptive messages contain carefully crafted job descriptions and application processes that appear legitimate, complete with official-looking branding and professional communication styles that mirror genuine Google recruitment correspondence.
Cyber researcher g0njxa identified this campaign while investigating broader patterns of credential theft operations targeting major technology companies.
The researcher’s analysis revealed that the threat actors employ multiple attack variations, adapting their techniques to evade detection while maintaining high success rates against unsuspecting victims.
Certificate Abuse and Evasion Techniques
The malware campaign demonstrates sophisticated evasion capabilities through the abuse of Extended Validation certificates across multiple platforms.
Threat actors have obtained legitimate Apple Developer ID certificates under names such as “THOMAS BOULAY DUVAL” and “Alina Balaban,” enabling their malicious applications to bypass initial security screening mechanisms.
The signed DMG files appear completely undetected on VirusTotal, achieving full undetected status across security vendors.
Analysis of the malicious launchers reveals deliberate attempts to legitimize applications by incorporating signer names into identifier strings, following patterns like “thomas.parfums” corresponding to “Thomas Boulay Duval.”
The Mach-O binaries contain embedded references that connect to remote AppleScript payloads, utilizing the Odyssey Stealer framework for credential harvesting operations.
The campaign’s infrastructure includes compromised domains such as franceparfumes[.]org hosting malicious scripts, with command and control servers operating from IP address 185.93.89.62.
These certificates represent significant financial investments for cybercriminals, as Apple’s developer certification process involves substantial time and monetary costs, making their eventual revocation impactful to ongoing malware operations.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.
The post Hackers Posing as Google Careers Recruiter to Steal Gmail Login Details appeared first on Cyber Security News.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A previously undocumented Android banking trojan called Klopatra has compromised over 3,000 devices, with a majority of the infections reported in Spain and Italy. Italian fraud prevention firm Cleafy, which discovered the sophisticated malware and remote access trojan (RAT) in late August 2025, said it leverages Hidden Virtual Network Computing (VNC) for remote control of infected devices and
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Microsoft is actively investigating and addressing widespread errors preventing users from accessing their mailboxes on Outlook.com.
The company has been providing regular updates throughout the day, indicating that targeted infrastructure restarts are gradually restoring service.
The issue, which began early on October 1, 2025, affects users attempting to log in or access their emails via the Outlook.com web interface.
While Microsoft has not detailed the full scope of the impact, user reports suggest a global outage, with many receiving error messages and being unable to view their inboxes.
The root cause has not been officially disclosed, but Microsoft’s response points towards a problem within the service’s underlying infrastructure.
Timeline of Microsoft’s Response
Microsoft’s support team has been working to resolve the issue, providing several updates on the service health status page.
Early in the morning, Microsoft acknowledged the problem and began its investigation. By 10:27 AM (GMT+5:30), the team was applying “smaller targeted reboots of affected infrastructure” and noted a gradual decrease in traffic errors as they monitored the service revert.
Updates around noon confirmed that engineers were continuing to “closely monitor service availability” and perform “additional targeted restarts where required.” These actions were aimed at stabilizing the platform and alleviating the impact on users.
By 1:07 PM (GMT+5:30), Microsoft reported observing “improvements in service availability following our targeted restarts.” The focus shifted to monitoring the service to ensure a full and stable recovery.
The most recent update at 2:33 PM (GMT+5:30) indicated that the team is continuing to see “steady improvements in service availability.”
Furthermore, Microsoft noted that the “backlog of messages is progressing as expected,” suggesting that email delivery delays that occurred during the outage are also being resolved.
While service appears to be returning to normal for many, Microsoft continues to monitor the situation closely to prevent any recurrence and ensure all systems are fully operational.
Users still experiencing issues are advised to check the official Microsoft 365 service status page for the latest information.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
The post Microsoft Investigating Widespread Outlook.com Outage Preventing Mailbox Access appeared first on Cyber Security News.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Security researchers have uncovered a new macOS malware campaign in which threat actors are abusing Extended Validation (EV) code-signing certificates to distribute completely undetectable (FUD) disk image (DMG) payloads. While EV certificate abuse has long plagued the Windows ecosystem, its expansion into macOS malware marks a significant escalation in code-signing exploitation. A fresh DMG sample […]
The post Hackers Abuse EV Certificates to Sign Completely Undetectable DMG Malware appeared first on GBHackers Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶


