As attackers increasingly leverage Scalable Vector Graphics (SVG) for stealthy code injection, security researchers face mounting challenges in detecting obfuscated payloads embedded within SVG assets.
The SVG Security Analysis Toolkit by HackingLZ offers a comprehensive solution: a suite of four Python-based tools designed to reveal hidden scripts, decode obfuscated URLs, and verify protection mechanisms, all without exposing analysts to unsafe execution environments.
Static and Dynamic Deobfuscation
The toolkit’s first two components extract.py and extract_dynamic.py work in tandem to uncover malicious scripts through both static and dynamic analysis:
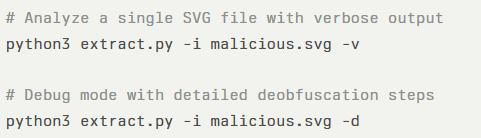
The extract.py is a static SVG URL Extractor that performs pattern-based analysis without executing any code.
It automatically detects and decodes XOR-encrypted payloads via String.fromCharCode patterns, Base64-encoded URLs extracted from data: URIsand character arithmetic schemes using parseInt and XOR loops. Usage examples illustrate its flexibility:
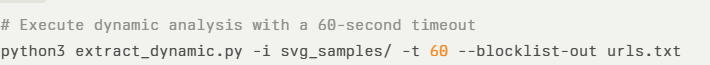
The extract_dynamic.py is a dynamic JavaScript Execution, leveraging box-js, safely executing embedded JavaScript within a sandbox to capture final URL constructions. Key features include:
- Advanced Hook System for monitoring location.assign(), window.open(), and AJAX calls
- Final URL Prioritization to distinguish complete URLs from partial fragments
- ActiveX/WScript Support for Windows-specific script monitoring
Protection Detection
To complete the analysis workflow, the toolkit includes cf_probe.py and encoder.py. The cf_probe.py is a Cloudflare Protection Detection program that scans HTTP and meta-refresh redirects for Cloudflare challenges.
This identifies Turnstile via data-sitekey attributes, scans linked JavaScript for reCAPTCHA or custom CAPTCHA systems, and reports CF headers like CF-Ray and DDoS protection messages.
The encoder.py is an SVG Test Case Generator; security teams can generate realistic obfuscated SVG samples to validate their detection pipelines.
- It supports six obfuscation patterns, including XOR + ES6 Proxy,
- Hex-encoded Function Constructor and Data URI scripts.
HackingLZ recommends the following analysis sequence for maximum coverage and safety:
- Generate Test Cases: encoder.py –random-all -o test_cases/
- Static Analysis: python3 extract.py -i test_cases/*.svg -v
- Dynamic Analysis: python3 extract_dynamic.py -i test_cases/ -o dynamic_results/
- Protection Verification: python3 cf_probe.py -i malicious_urls.txt
By combining static string decoding, sandboxed script execution, protection detection, and controlled test data generation, the SVG Security Analysis Toolkit empowers defenders to stay ahead of evasive SVG-based phishing and malware campaigns.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
The post SVG Security Analysis Toolkit to Detect Malicious Scripts Hidden in SVG Files appeared first on Cyber Security News.



.webp)
.webp)
.webp)