Chromium-based browsers, including Chrome, Edge, and Brave, manage installed extensions via JSON preference files stored under %AppData%\Google\User Data\Default\Preferences (for domain-joined machines) or Secure Preferences (for standalone systems).
Synacktiv research indicates that by directly altering these files, attackers can make the browser load any extensions without the user’s consent or involvement from the Chrome Web Store.
A successful compromise involves three technical prerequisites: pre-calculating the extension ID, generating valid Message Authentication Codes (MACs) for both the extension entry and the developer_mode flag, and bypassing enterprise policy controls.
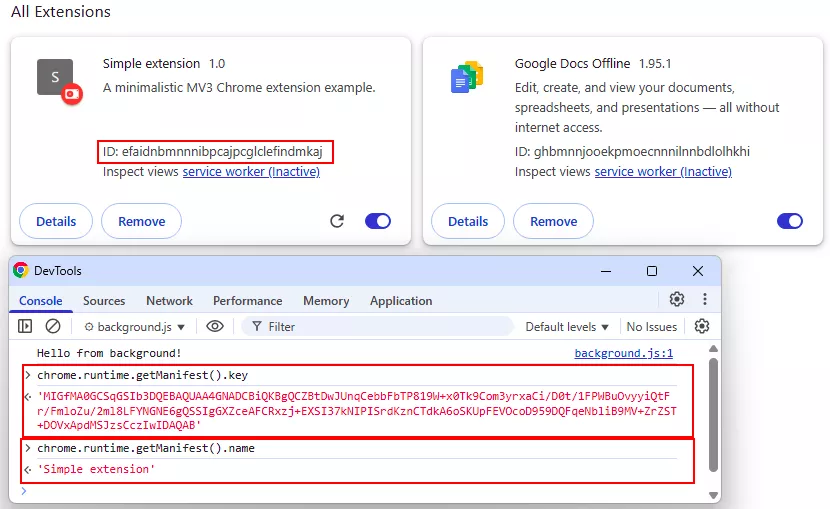
Extension IDs are deterministically derived from the extension’s public key or installation path via a SHA-256 hash truncated to 32 hex characters and mapped to a custom alphabet (a–p).
Chromium’s integrity checks use an HMAC seeded with a static value extracted from resources.pak specifically resource file 146 to sign critical JSON keys.
Attackers reverse this HMAC algorithm to compute valid MACs for extensions.settings.<crx_id> and extensions.developer_mode, enabling silent registration of their backdoor extension.
Bypassing Chrome Extension GPO Controls
Enterprise environments commonly deploy GPOs to whitelist or blacklist extensions through policies like ExtensionInstallAllowlist and ExtensionInstallBlocklist.
Three advanced evasion methods undermine these controls:
Synacktiv stated that by reusing the RSA public key of a corporate-approved extension (e.g., Adobe Acrobat Reader for Chrome), an attacker generates a matching extension ID.
They then inject a malicious unpacked extension under that ID, bypassing hash-based allowlists.
When an unpacked extension and a store-installed extension share the same ID, Chromium prioritizes the unpacked version. This collision allows attackers to override trusted plugins stealthily.
Windows applies policies in LSDOU order. Although Chrome policies reside under HKCU\Software\Policies\Google\Chrome, a local administrator can delete or modify the registry entries, removing allowlists or blocklists to sidestep policy enforcement entirely.
Leveraging these techniques, threat actors can deploy extensions that intercept network traffic, scrape session cookies, execute background service workers, and inject content scripts into targeted web pages.
A proof-of-concept toolkit from Synacktiv demonstrates remote SMB-based deployment alongside a custom C2 server, enabling JavaScript execution within the browser process and undermining protections such as App-Bound Encryption.
Securing against this vector requires monitoring for unauthorized changes to preference files, validating registry policy integrity, and detecting anomalous extension registrations.
Without such detection mechanisms, “phantom extensions” offer a stealthy, persistent route to enterprise-wide data exfiltration and lateral movement.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
The post Hackers Can Compromise Chromium Browsers in Windows by Loading Arbitrary Extensions appeared first on Cyber Security News.





.webp)
.webp)