SonicWall has issued an urgent advisory urging all customers to perform an Essential Credential Reset after security researchers discovered that MySonicWall configuration backup files were inadvertently exposed on public storage.
The sensitive files contained encrypted passwords, pre-shared keys, and TLS certificates used by SonicOS appliances, potentially allowing threat actors to decrypt and leverage credentials to gain unauthorized network access.
SonicWall’s Knowledge Base outlines three critical phases: Containment, Remediation, and Monitoring, to mitigate risk and restore secure operations.
Lock Down WAN-Facing Management
To immediately reduce exposure, SonicWall recommends disabling or restricting all WAN-based management services before proceeding with password resets.
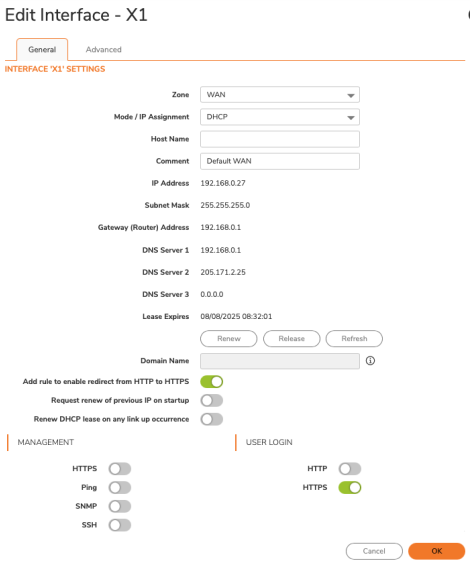
Administrators must navigate to Network → System → Interfaces, edit each WAN interface, and disable HTTP/HTTPS & SSH Management.
Disable the HTTPS/SSH Management options
Similarly, SSL VPN and IPsec VPN services should be turned off by accessing Network → SSL VPN → Server Settings and Network → IPsec VPN → Rules and Settings, respectively.
SNMP v3 access must be disabled under Device → Settings → SNMP to prevent unauthorized SNMP GET/SET commands from exposing Engine IDs or community strings.
Restricting inbound NAT/Access Rules to known/trusted IP addresses further prevents attackers from reconnecting after credential changes.
SonicOS 6.5.5.1 and 7.3.0 feature a dynamic enforcement option that blocks user accounts until a new password is set, ensuring containment remains effective even if WAN restrictions cannot be fully applied.
Credential Reset
Key actions include resetting passwords for all Local Users and re-enrolling TOTP bindings.
Administrators must update bind account passwords on LDAP, RADIUS, and TACACS+ servers, rotating shared secrets with SHA-256-hashed values.
Rotate shared secrets
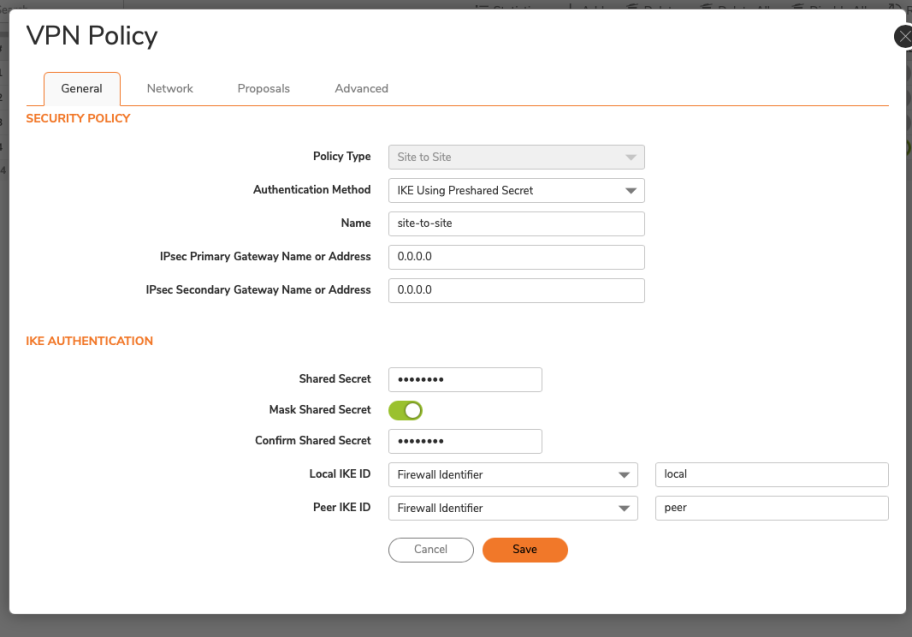
All IPsec VPN pre-shared keys—used for both site-to-site tunnels and GroupVPN require replacement with new AES-256 encrypted secrets, with corresponding updates on remote gateways.
WAN interface credentials for L2TP/PPPoE/PPTP and cellular WWAN must be refreshed in coordination with ISPs. Dynamic DNS, Clearpass NAC, and email log automation accounts should have their passwords reset to avoid delivery failures.
Finally, update encryption keys in the Global Management System (GMS) IPSec Management Tunnel mode under Device → Settings → Administration, reads the Knowledge base.
After remediation, re-enable services gradually, verifying each with a successful login test and SSH key rotation. Customers relying on automated workflows are reminded to update scripts referencing the old credentials.
Continuous monitoring of the system and audit logs is essential. Administrators should review Monitor → Logs → System Logs and Audit Logs, filtering for repeated authentication failures or anomalies in configuration changes.
Export logs to CSV for detailed analysis, and leverage SIEM integrations using Syslog over TLS 1.2 to ensure secure forwarding.
Following these steps will safeguard SonicWall environments against exploitation of exposed configuration backups and reinforce the integrity of network perimeter defenses.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.
The post SonicWall Urges Customers to Reset Login Credentials After Configuration Backup Files Exposed appeared first on Cyber Security News.